
Every year, Microsoft invests over a billion dollars into security, including the security of the Azure platform, so that your information and business resources can be protected from cyber threats. It has become the most trusted cloud based platform by providing a secure foundation across infrastructural and operational security. In this blog, we would be discussing the top reasons why Azure is the most flexible and secure platform and some interesting facts about Microsoft Azure cloud.
Table of Contents
Toggle
Table of Contents
ToggleWhat is Azure?
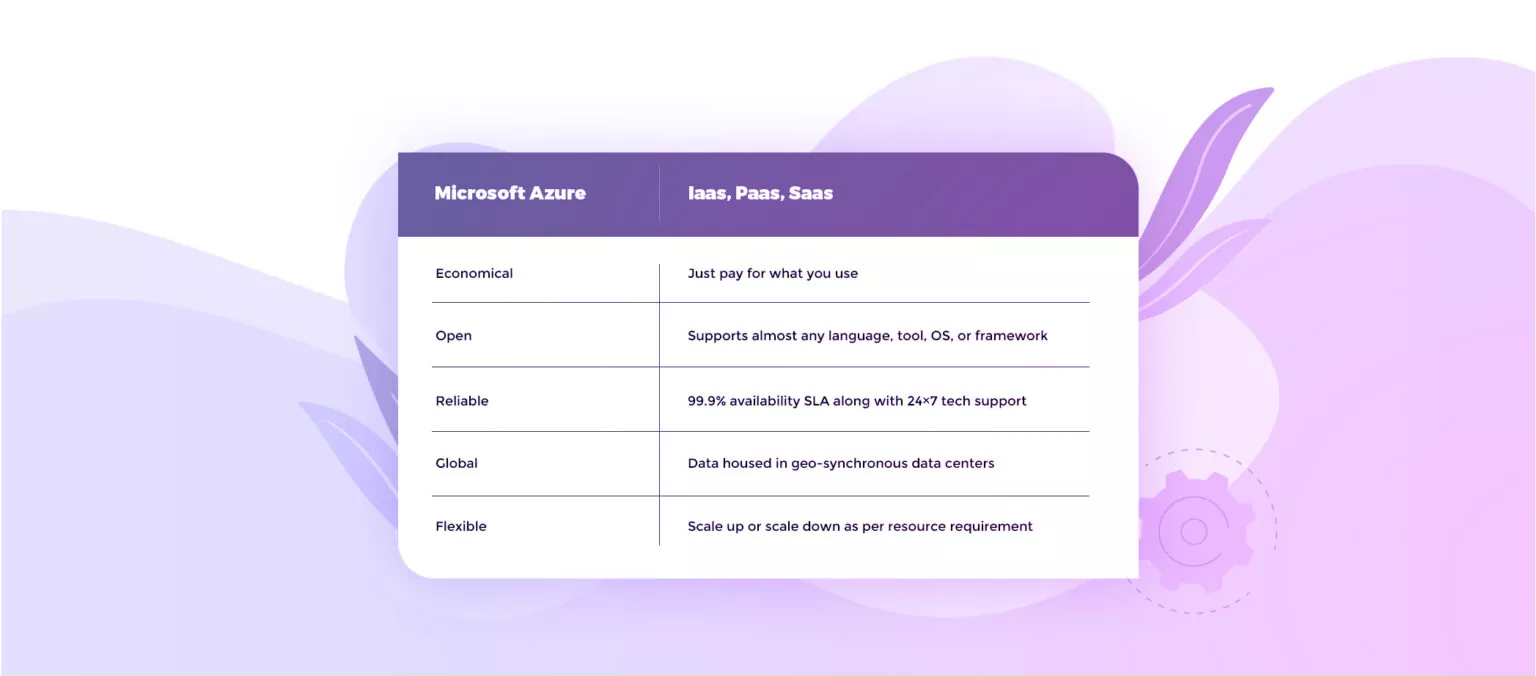
Azure is a fast and flexible public cloud computing platform offering cloud based solutions – IaaS, PaaS, and SaaS. Let’s catch up on some quick facts about Azure.
Why is Azure Secure?
Microsoft’s investment across infrastructure, hardware, and specialists are huge and unmatched. Microsoft gives a protected framework to our datacenters, made out of isolated networks, well-maintained equipment and firmware, and industry-driving operational security measures with the goal that you can have more assets accessible to convey business esteem. Let’s find out reasons why Azure is considered the most flexible and secure cloud platform.

The Ultimate Guide To Cloud Cost Optimization
Flexibility and Disaster Recovery
Azure is a disaster recovery dream tool that requires minimal maintenance. It is innately flexible – a user can backup data in almost any language, any OS, and from any location. Also, you are given a choice to backup your data on a daily, monthly, or weekly basis. It charges you only for what you use and gives you the option to scale up or scale down your resources as per your business requirements.
Azure site recovery enhances tape backup with offsite replication up to ninety years of data retention and requires minimal operational costs and negligible capital investment.
Secure Network Infrastructure
Adopting cloud is an agile approach that reduces infrastructure costs and gives us the freedom to scale up and scale down our resources as per our needs. The Azure network (management network) and customers network are shared, but Microsoft has several mechanisms to ensure that Azure’s network and customer’s network remain secure and segregated. The management network is looked after by Microsoft and in case devices or administrators want to connect to Azure, there are controls such as just-in-time access and workstations with limited accessibility to avoid unauthorized individuals from gaining access to the Azure network.
Data on Azure are always in an encrypted format while in transit except in the customer-controlled network. It also has an in-built mechanism to protect against DDoS (distributed denial-of-service) attacks. They are busy continuously monitoring the traffic profiling and detect the attacks in any.
Secure Hardware and Firmware
Security controls are in-built in the firmware and hardware of Azure to ensure security throughout its lifetime. For firmware, a chip made of CPU, programmable input/output called Cerberus protects against malicious updates and illegal access. Also, firmware goes through routine reviews to mitigate the threat before it impacts the business. The hardware has the access to boot environment before OS loading so that it can detect malicious code if any and stop them.
Azure is the first cloud platform that facilitates software and hardware-based trusted execution environments. Hyper-V and Intel SGX chip-enabled servers are used in computing to bifurcate execution and data.
Secure Testing and Monitoring
Microsoft has more than 3,500 network safety specialists who work for your benefit 24x7x365. This number incorporates more than 200 experts who identify possible vulnerabilities through red and blue group team exercises. The red group attempts to compromise Azure’s structure, and the blue group shields against attacks made by the red group. This makes team become pro in detecting and responding to cyber-attacks.
Microsoft utilizes cybersecurity specialists to protect your infrastructure, so your assets can be accessible for other business activities.
The basic DDoS protection is enabled by default in the platform, moreover, you can also use the Azure DDoS protection standard to protect against layer 3-7 attacks. For instance, it can secure against volumetric attacks like amplification floods, UDP floods, or attacks targeting IPv4 and IPv6. The Layer 3 and Layer 4 attacks are distinguished and are sent to the scrubbers. Scrubbers decide whether the traffic is malicious or not and if it’s protected to go through the network. At Layer 7, we can secure against attacks focusing on HTTP and SQL protocols. This is why Azure is secure and a preferred platform.
To learn more about Microsoft cloud services, Security, and flexibility, you can visit our website and check out the latest blogs on Microsoft Azure cloud.
Additionally, if you are in search of skilled Azure Professionals such as Azure engineers, Azure architects, and more, PeoplActive can help you with that. It is a platform involved in the remote hiring of Azure talents from worldwide and brings them to the organizations which need them the most.




