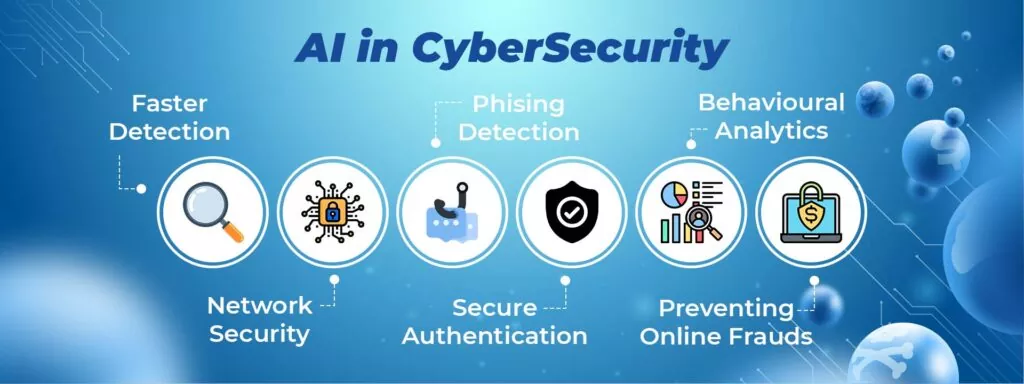
With advancements in technology, hackers are getting enough smart in finding loopholes in networks and crack in corporate security systems. Post that what may happen, you all very well know it. But, Artificial Intelligence has acted as a big savior here. Let’s find out what are the basics of AI cybersecurity, its subsets, the benefits of using AI in cybersecurity, and more. Let’s get started.
Understanding AI Basics

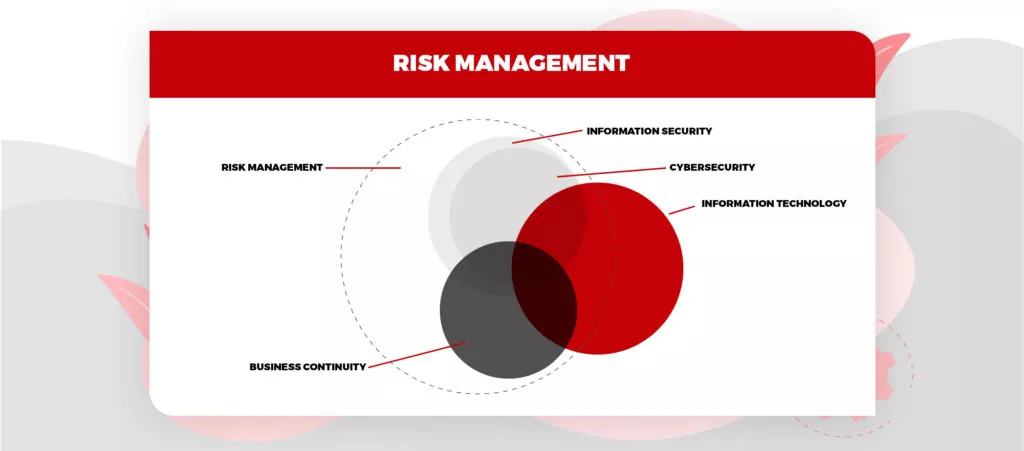
Artificial Intelligence refers to the technology that can comprehend, learn, and act dependent on obtained and inferred data. Today, artificial intelligence in cybersecurity works in three ways:
- Assisted Intelligence – broadly accessible today, further develops what people and organizations are already practicing.
- Augmented Intelligence – emerging today, empowers organizations to do things they couldn’t in any case do.
- Autonomous Intelligence – being developed for the future, for eg – self-driving cars.
Also Read – Cyber Attacks on Utilities Are Spiking. Is Your Company Prepared?
Subsets of AI Technology today are as follows –
- Machine Learning – It uses strategies to enable computer systems to learn with the help of data rather than being explicitly programmed. ML works best for focused tasks rather than a wide-going mission.
- Expert Systems – These are programs intended to take care of issues inside the specialized domains. By copying human thinking, they tackle issues and settle on choices utilizing fuzzy standards-based reasoning through cautiously organized collections of data.
- Neural Networks – It utilizes organic programming which empowers computers to learn from observational information. In a neural network, every node relegates a load to its input addressing how correct or erroneous it is comparative with the activity being performed. The result is then dictated by the sum of such loads.
- Deep Learning – It is a part of machine learning based on learning data representation, rather than task-explicit algorithms. In today’s world, image recognition is done through deep learning gives better results than done by humans.
Image Source: IEEE
Benefits of Using AI in Cyber Security

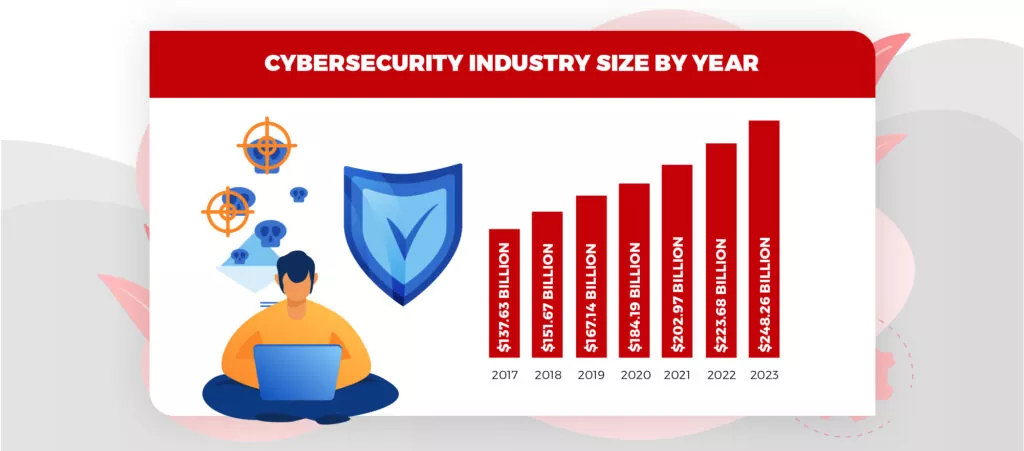
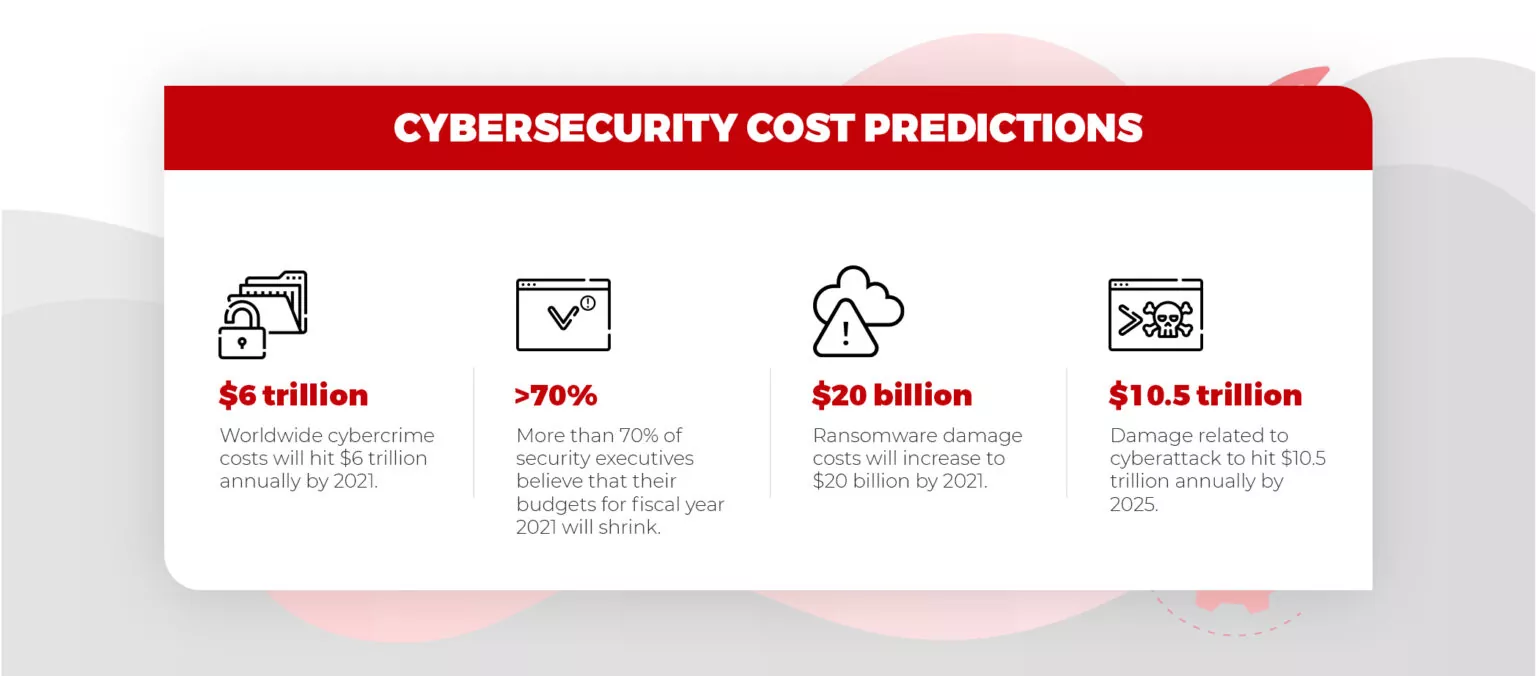
The growth rate of cybercrimes is consistent with the development of technology. As technology expands, the surface for cybercrimes also expands. Let’s find out how Artificial intelligence in cybersecurity has played a heroic role in securing the networks.
AI Learns More Over Time
AI Technology is intelligent and keeps improving network security over time. With the help of machine learning and deep learning, it recognizes the patterns and behavior of the network. If there is any deviation in the network security, it proceeds to detect the incident and respond accordingly. Artificial neural networks learn the patterns passing through the network which makes the security stronger with time.
AI keeps learning and making the network stronger over time which makes it difficult for the hackers to beat the intelligence. The use of AI in cyber security weakens the hacker’s activities and strengthens the overall network security.
Artificial Intelligence Identifies Unknown Threats
A human being can’t identify all the threats that an organization may face because hackers dispatch countless attacks with various intentions. Unknown threats can make gigantic harm to an organization. Therefore, organizations work their best to detect, identify and prevent these attacks ASAP.
As attackers attempt new strategies from complex social engineering to malware attacks, we also need to come with advanced methods to nullify their activities and secure our systems. Artificial Intelligence has shown to be probably the best innovation in planning and preventing unknown threats that may harm business a lot.
AI Cybersecurity Can Handle a Lot of Data
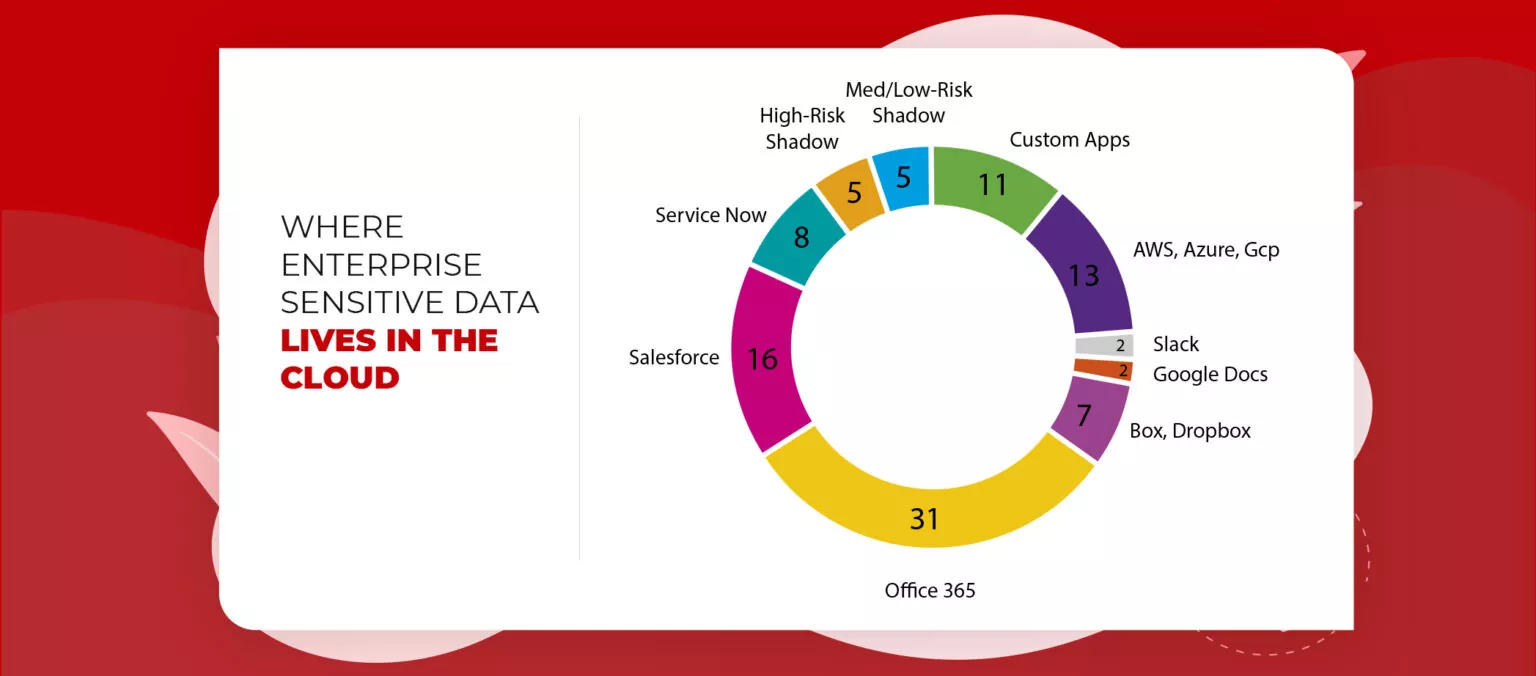
A great deal of activity occurs on a company’s network. A normal fair-sized organization itself has huge traffic. That implies there’s a great inflow and outflow of data between clients and customers on daily basis. This information needs to be protected from hackers and their malicious codes. However, at that point, network protection staff can’t actually look at all the traffic for potential threats.
Artificial intelligence is the best solution that will assist you with distinguishing any threats masked within normal activities. Technology that utilizes AI, can easily recognize and distinguish any dangers concealed in the chaotic traffic.
Also read: Cyber Security vs Information Security
Better Vulnerability Management
Vulnerability assessment and management are critical in order to secure the company’s network. As referenced before, a mid-sized organization manages numerous threats every day. It needs to distinguish, recognize and prevent them to be safe. Breaking down and surveying the current safety efforts through AI research can help in vulnerability management.
Artificial intelligence in cybersecurity assists you with evaluating systems faster than staff does, expanding your problem-solving ability manifold. It distinguishes vulnerable points in computer systems and business networks and helps organizations concentrate on significant security errands. That makes it conceivable to oversee weaknesses and secure business frameworks on schedule.
Overall Better Security
Threats keep changing with time as hackers change their strategies consistently. That makes it hard to focus on security errands at an organization. You might need to deal with phishing alongside a denial-of-service attack or ransomware.
These attacks have comparable potential yet you should realize what to manage first. Bigger threats that can make organization security vulnerable are human carelessness. Therefore, to ensure the security of your system, deploy AI on your network to distinguish possible threats and assist you to prevent them.
Duplicative Process Reduce
As mentioned before, attackers change their strategies frequently. But our fundamental security best practices continue to be the same. It’s a tendency of a human being to get bored of daily work and take it for granted. But doing so may put the organization’s security at a risk. So, let’s find out how AI can help in such a scenario.
AI covers this shortcoming of human beings and can easily look after the duplicative cybersecurity processes that can irritate the staff. It investigates the network in depth whether there are security loopholes that could be harming to your organization.
Securing Authentication
There are websites that contain a page demanding the personal details of visitors to get the service or purchase items. They contain contact forms where visitors need to share sensitive information. In such cases, companies need an extra security layer to run such websites as they contain personal data. The extra security layer will guarantee that your visitors are protected while browsing your website.
Artificial intelligence gets verification whenever a client needs to sign into their record. AI cybersecurity utilizes different devices like CAPTCHA, and finger impression scanners to verify the user. The data gathered by these elements can assist with recognizing in case a sign-in is genuine or not.
Also Read – The Power of AI and Machine Learning in Cloud Security Automation
Hire Cybersecurity Experts for Your Critical Projects
Having a cybersecurity specialist team has become a necessity for every business. Are you looking for cybersecurity experts for your projects? If so, PeoplActive is a one-stop solution for you.
PeoplActive is an IT consulting company and also offers staffing/staff augmentation services to our clients for both PERM and Remote roles. We specialize in the cloud and cyber security roles however, that does not limit our expertise, we also assist our clients with different complex IT roles like Full Stack, Mean Stack, Data Engineers, iOS or Android, etc.
Our tech-savvy recruiters are well-versed with the latest technology, programming knowledge, and other skills which help them better understand the job description and bring exceptional talents to your dream team.
- Joining Turn Around – 2 to 4 weeks.
- Avg. placement Percentage – More than 90%
- Geographies – US, India, UAE, and ANZ.
- Flexible hiring model – Contractual or Permanent.
- Specialization – Cyber Security, all cloud platforms, DevOps, Architect, Data Engineers, etc.
We hope you found the blog useful and informative. In case, you have any talent-hiring requirements, let us know today. Looking forward to hearing from you.