
Cloud migration is at its peak across the globe as it’s the most advantageous and savvy method of managing big data. As per Gartner, in the consequence of the Covid-19 pandemic, the overall end-client spending on public cloud administrations is forecast to grow 18.4% in 2021 to add up to $304.9 billion. This quick transition has naturally caught the attention of cybercriminals who are exploiting weaknesses present in cloud-based data to deploy malware. How safe is the cloud storage? In this blog, we would be throwing light on some mindboggling facts & stats on cloud security and how to secure data in cloud computing, and much more.
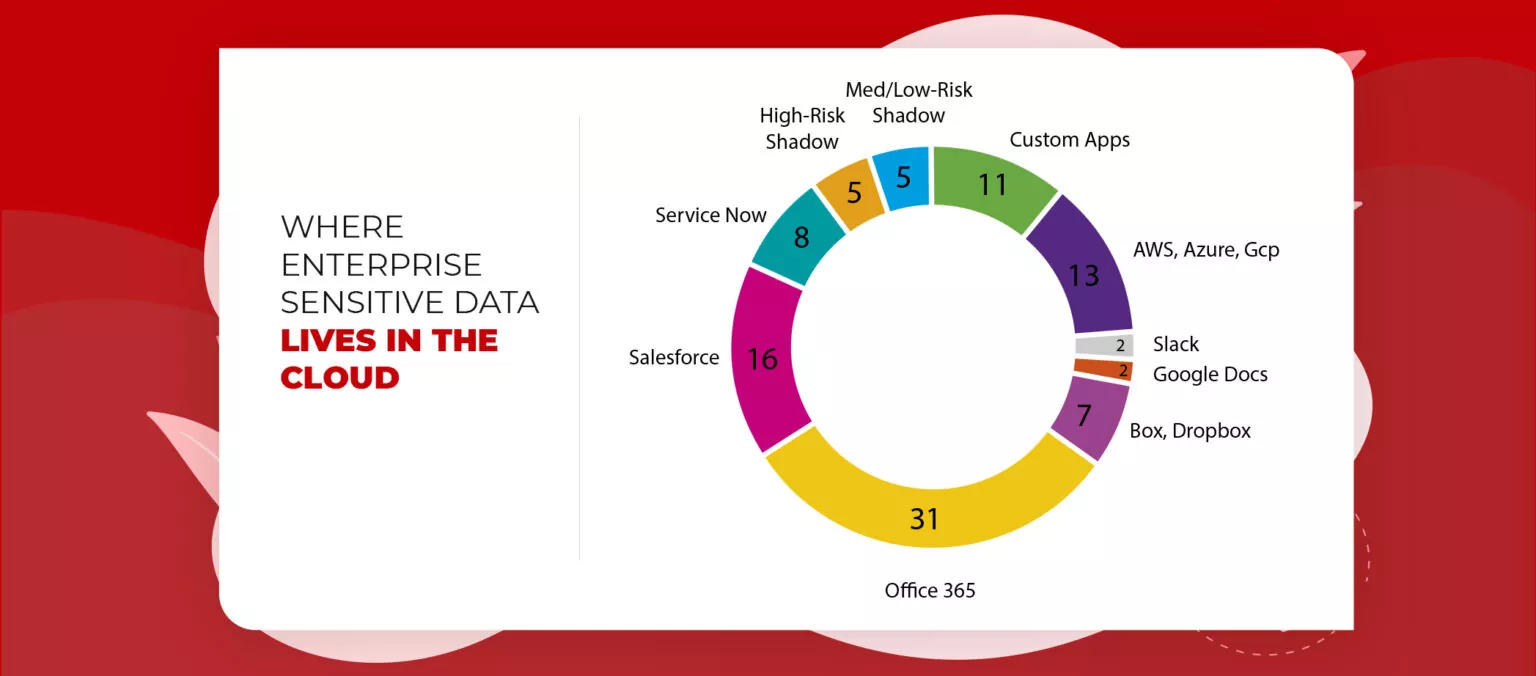
Table of Contents
ToggleSo, let’s get started…..
Cloud Computing Security Challenges
In today’s fast and furious world, data is the king that has helped organizations to provide customized services. Every organization wants its data to be secure and accessible from anywhere in the world. Cloud technology has made this dream come true but also invited few cloud infrastructure security challenges. To reap cloud benefits, they need to recognize the insecurities and choose the right tools to mitigate them with the help of cloud security experts. Let us have a look at some of the key cloud computing security challenges enterprises have been facing so far.
ALSO READ: Next Silicon Valley is Nowhere – It’s in the Cloud
Security Challenge 1: DDOS and Denial of Service Attacks
With time, cloud data operation is maximizing, and therefore cloud information security is turning into a greater target for a cyber attack. Distributed Denial of Service (DDoS) assaults are more frequent than ever before. A DDoS attack is intended to overpower website servers so it can’t react to authentic client requests. In case a DDoS attack is successful, it inactivates the websites for some hours or even days. This can bring a loss of income, client trust, and brand authority. However, it’s a necessity to complement cloud services with DDoS assurance for cloud infrastructure security.
Security Challenge 2: Insecure Access Control Points
One of the extraordinary advantages of the cloud is that data can be accessed from any place and from any device/system. Imagine a scenario in which the interfaces and especially the application programming interfaces (APIs) clients cooperate with aren’t secure, what can be the repercussions? Hackers can discover and access these sorts of weaknesses and exploit credentials through APIs whenever given chance. There are many web application firewalls used to analyze HTTP requests to guarantee if they are authentic traffic. Execute them with the help of cloud security experts to shield web applications and APIs from security breaks within the cloud environment that are not on-premises.
Security Challenge 3: Data Breaches
In May, 2021, a cyber attack on the largest US fuel pipeline has closed the entire 5,500-mile pipeline leading to the shutdown of cross country gas pipeline system. There are many more such stats that emphasized the growing challenges to data security on cloud.
Generally, IT experts have had incredible command over the organization’s infrastructure and physical hardware (firewalls, and so forth) securing restrictive data. In the cloud (in all situations including private cloud, public cloud, and hybrid cloud circumstances), a portion of those security controls is shared or given to some trusted partner which can build security risk chances. Picking the right vendor, with a solid record of executing strong security measures, is essential to protecting data in the cloud and beating cloud data breach challenges.
Security Challenges 4: Notifications and Alerts
Awareness and proper communication of security threats are very important for cloud computing security. Alarming the attacked websites or application managers when a threat is recognized should be a part of cloud data security. With the help of prompt communication, needful steps can be taken to mitigate the impact of the threats and protecting data in the cloud.
Why Company Needs Data Protection in the Cloud?
Companies are gathering massive data on the cloud ranging from confidential to fairly less critical information. But it’s not a cakewalk journey, a team of cloud cyber security experts is always awake and continuously working to remove any loophole in cloud infrastructure security that may give opportunities to hackers to ruin data. For protecting data in the cloud, they need to be well aware of –
- Which data they have and where it’s located.
- Which data they need to protect and at what level.
- Which applications are being accessed and by whom.
- Which data is exposed, how it’s exposed, and potential risks.
- How customers are accessing data their cloud applications
With the help of all this information, organizations put a steady and automated cloud information assurance offering – that assists them to find, screen, ensure, and secure their applications and data security on cloud.
Cloud Security Failures and Pitfalls Companies Facing
There have been several prominent cloud security attacks in the past years that have caught the attention of businesses. There are some common failures and pitfalls that have resulted in challenged the data security on cloud. Therefore, with the help of cloud security engineers and other cloud experts, organizations keep an eye on cloud security – assessing the loopholes they have become prey to. Let us go through some common Loopholes or ignorance –
Ignorance of Emerging Cloud Threats
Companies have disregarded or don’t pay attention to the arising cloud security threats. As the Cloud advances and changes into refined framework and innovation, so is the cloud security attacks. Hackers are getting stronger with time have built advanced techniques to exploit any chance to penetrate and take out information. Therefore, it is a necessity for cloud experts to stay updated with the ongoing security threats and possible solutions for data protection in the cloud.
Weak Credentials for Inner Cloud
A data breach in 2015, at The Health Insurer Anthem Inc., affected 80 million of its customers, was due to mishandled user credentials. This organization failed to employ two-factor (multiple authentications) user access controls. After this pathetic incident, organizations have started utilizing multi-factor authentication and also hard to crack credentials to ensure data security on cloud.
Employees of the organization are trusted enough with sensitive data and information. Few of them may have unhindered admittance to all confidential information in the company’s computer systems. Sometimes, unintentionally, they make data modifications and leak the data using the access credential, and become victims of cybercrime.
ALSO READ: How to Organize Your Cloud Security Team



