

What Are the Different Roles in Cybersecurity and Which Expert Do You Need
As cybercrime continues its relentless rise, businesses in every sector face a pressing need to hire cyber security developers and professionals to safeguard their networks, systems, and data from potential threats. However, with various types of cybersecurity roles available, determining which cybersecurity expert to hire can be a challenging task.
In this blog, we will simplify this process by exploring the diverse world of cybersecurity professionals. By understanding the unique skill sets each role demands, you will be better equipped to make informed decisions and fortify your organization against the ever-evolving landscape of cyber risks. Let’s embark on this crucial journey together to secure your business’s future in an interconnected world.
What makes Cybersecurity crucial in today’s world?
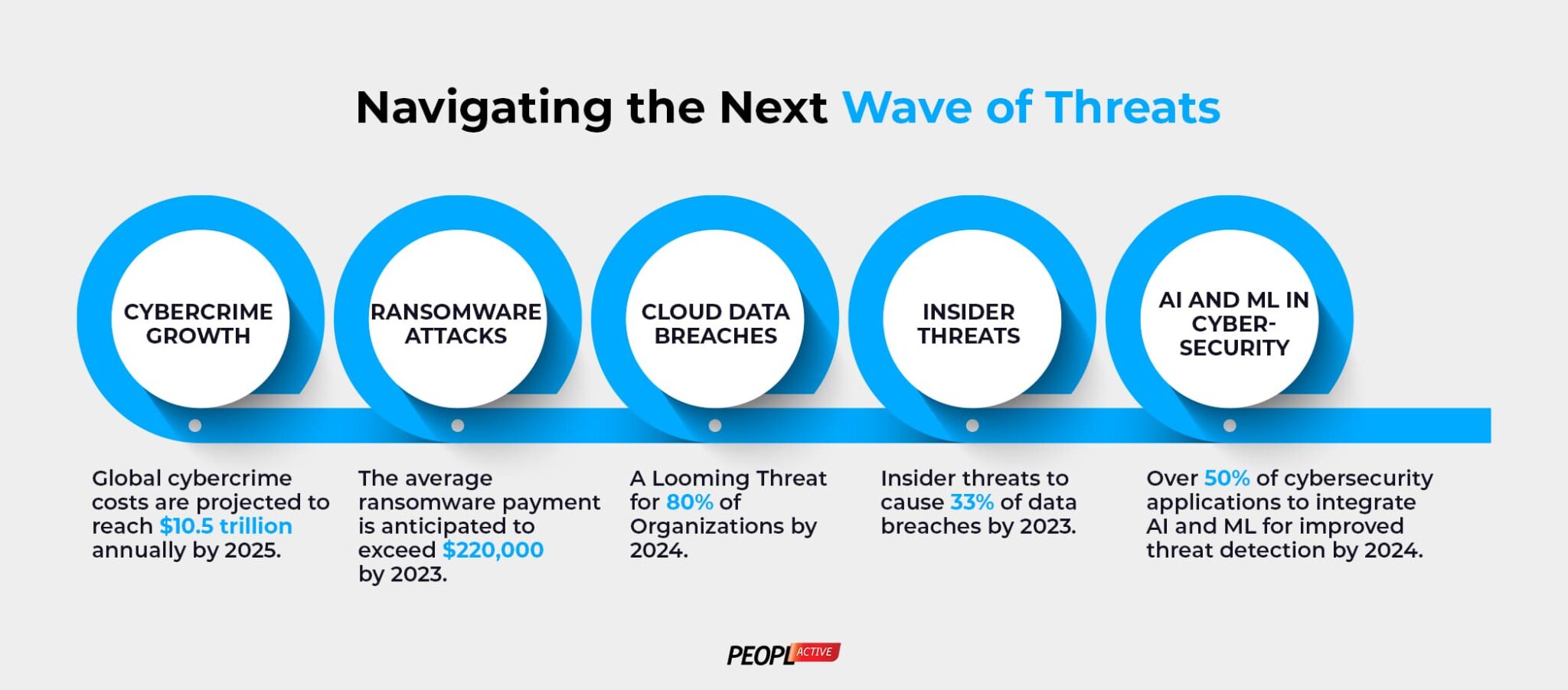
Whether you operate a small enterprise or a large corporation, chances are that you heavily depend on digital solutions to store, organize, and retrieve sensitive business-related data. Such information may encompass various sensitive elements, including but not limited to:
- User credentials (usernames and passwords)
- Financial details (banking information)
- Personal identification data (social security numbers)
- Payment card particulars (credit card information)
- And a plethora of other sensitive data.
By implementing effective cybersecurity measures, you safeguard crucial information from falling into the hands of malicious hackers who seek to exploit it. However, not all cybersecurity analysts possess the same skill sets and expertise. So, how do you determine the specific experts you should bring onboard to strengthen your defense? While your hiring requirements are unique to your business, there are several types of cybersecurity professionals that every company should consider. Let’s explore these essential roles and the value they bring to bolstering your cybersecurity strategy.
Top Cybersecurity Roles
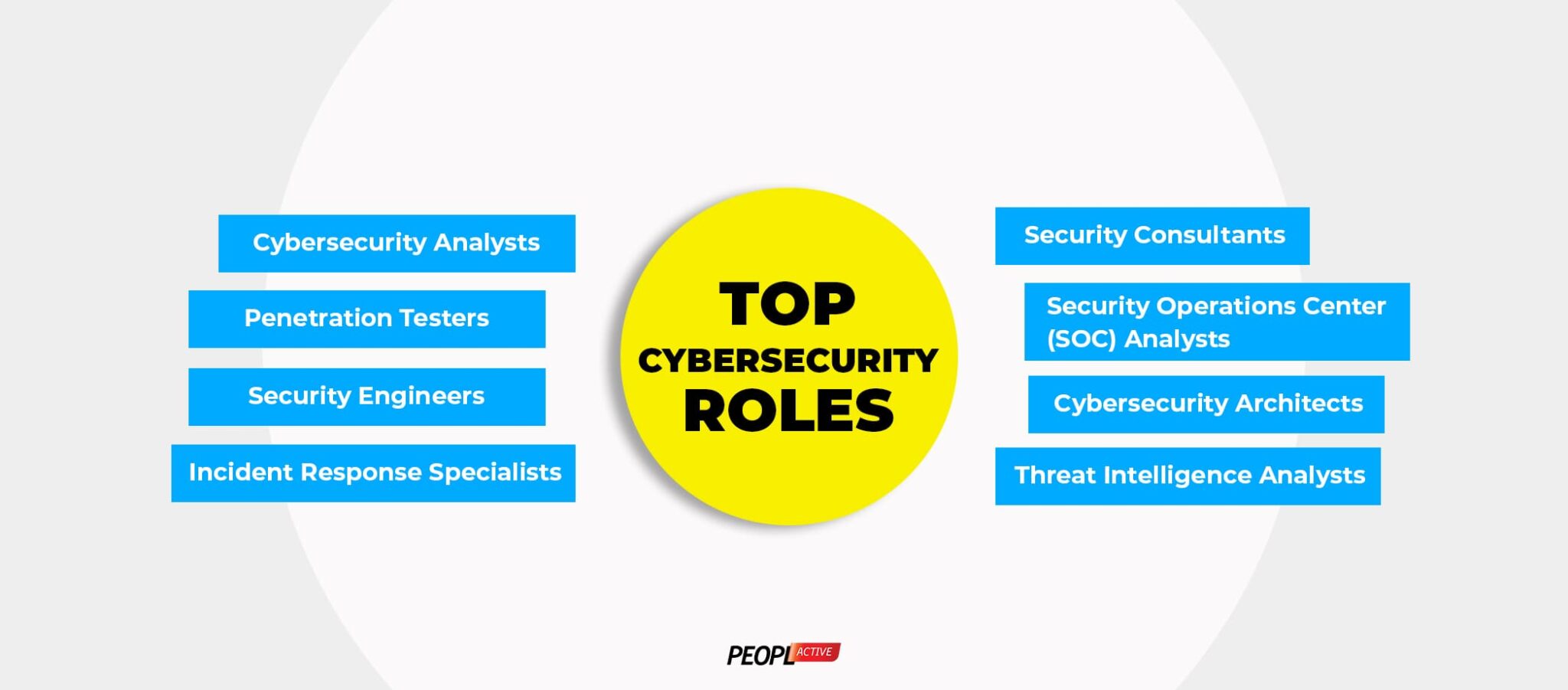
For organizations seeking an impenetrable shield against cyber threats, hiring Cyber Security Experts is paramount. These top cybersecurity roles represent key players in safeguarding businesses from the ever-growing menace of cyberattacks. With their specialized expertise and unique responsibilities, these skilled professionals serve as an essential line of defense, protecting valuable assets and sensitive information from malicious actors.
Role 1: Cybersecurity Analysts
Why Should You Hire Cybersecurity Analysts?
- Detection and Response: Cybersecurity analysts serve as the first line of defense against an ever-growing array of cyber threats. Their primary responsibility is to continuously monitor networks, systems, and applications to detect any suspicious activities or security breaches. With the “2022 Cyber Threat Report” by Accenture reporting a staggering 125% increase in cyberattacks in the past year, hiring cybersecurity analysts ensures you have a dedicated team of professionals ready to swiftly identify threats and respond with effective countermeasures.
- Preventing Significant Damages: The same report highlights that a remarkable 87% of cyberattacks were blocked at an early stage, showcasing the indispensable role played by cybersecurity analysts in preventing significant damage to your organization. By employing cybersecurity analysts, you strengthen your ability to detect and neutralize threats before they escalate.
Role 2: Penetration Testers (Ethical Hackers)
The Crucial Role of Penetration Testers
- Proactive Vulnerability Assessment: The rise of cyber threats has prompted organizations to adopt a proactive approach to cybersecurity. Penetration testers, often referred to as ethical hackers, simulate real-world attacks to identify vulnerabilities before malicious actors can exploit them. The “2023 Cybersecurity Insights” by Cybersecurity Ventures reveals that 70% of organizations now conduct regular penetration tests, a significant increase from 56% in the previous year. Hiring penetration testers allows you to discover and patch critical vulnerabilities, thereby averting potential security disasters.
- Averting Security Disasters: By identifying and addressing vulnerabilities proactively, penetration testers play a crucial role in preventing security incidents that could otherwise lead to data breaches, financial losses, and reputational damage.
Also Read: Phishing Attacks Targeting Cloud Services and SaaS Platforms
Role 3: Security Engineers
Why Should You Hire Security Engineers?
- Strengthening Digital Infrastructure: With the rapid adoption of cloud services and digital transformation, security engineers have become indispensable in strengthening an organization’s security infrastructure. The “State of Cybersecurity 2023” report by PwC indicates that 78% of companies have increased their investment in security engineers to protect their digital assets. Hiring security engineers ensures your organization is well-equipped to defend against cyber threats and can maintain business continuity.
- Protecting Digital Assets: Security engineers play a vital role in designing, implementing, and managing security solutions to safeguard your organization’s digital assets. Their expertise in configuring firewalls, encryption technologies, and other security tools fortifies your defenses against potential cyberattacks.
Role 4: Incident Response Specialists
Why Should You Hire Incident Response Specialists?
- Effective Breach Management: The dynamic nature of cyber threats demands a well-defined incident response plan. The “2023 Data Breach Investigations Report” by Verizon revealed that 73% of data breaches were financially motivated, while 10% were driven by espionage. Hiring incident response specialists ensures you have professionals who can effectively manage and contain breaches before significant damage occurs.
- Swift Identification and Response: The same report highlighted that 75% of breaches took days or longer to discover, further underscoring the need for well-trained specialists who can swiftly identify and respond to threats. Incident response specialists can help minimize the impact of potential breaches through swift and efficient actions.
Role 5: Security Consultants
Benefits of Hiring Security Consultants?
- Expert Guidance: As businesses grapple with the complexities of cybersecurity, many are turning to external security consultants for expert guidance. The “2023 Cybersecurity Trends Report” by EY stated that 82% of organizations engaged security consultants to assess their security strategies and protocols. Hiring security consultants ensures your organization benefits from objective assessments and actionable recommendations.
- Assessing Security Strategies: Security consultants bring an unbiased perspective and a wealth of experience to your cybersecurity strategy. They can help your organization identify strengths and weaknesses in its current approach, aligning your security efforts with industry best practices.
Role 6: Security Operations Center (SOC) Analysts
Why Should You Hire Security Operations Center (SOC) Analysts?
- Real-Time Monitoring: SOC analysts are responsible for real-time monitoring of an organization’s security infrastructure, including network devices, servers, and endpoints. They use advanced security tools and technologies to detect and respond to security incidents as they happen.
- Incident Triage and Escalation: SOC analysts play a pivotal role in incident triage, assessing the severity of security events and escalating critical incidents to higher-level security teams for immediate attention. Their swift actions can help prevent major security breaches.
- Threat Intelligence Analysis: SOC analysts analyze threat intelligence data to stay abreast of emerging cyber threats and trends. By proactively adopting security measures based on this intelligence, they bolster an organization’s defenses against evolving threats.
Role 7: Cybersecurity Architects
Why Should You Hire Cybersecurity Architects?
- Creating Comprehensive Security Blueprints: Cybersecurity architects design and build a comprehensive security framework that aligns with your organization’s specific needs and compliance requirements.
- Ensuring Scalability and Flexibility: They ensure that security measures are scalable and adaptable to accommodate future technological advancements and business growth.
Also Read: Approaches in Network Security for Businesses
Role 8: Threat Intelligence Analysts
Why Should You Hire Threat Intelligence Analysts?
- Proactive Threat Monitoring: Threat intelligence analysts specialize in monitoring and analyzing emerging cyber threats and trends. By continuously tracking the cyber landscape, they can provide your organization with early warnings and proactive strategies to counter potential attacks.
- Strategic Decision-Making: These analysts offer critical insights to help leadership teams make informed decisions about cybersecurity investments, resource allocation, and risk management.
Why is it so hard to hire cyber security developers?
In today’s digital age, hiring cybersecurity developers has become a formidable task, with the ever-increasing demand for skilled professionals in the face of an evolving threat landscape. The scarcity of qualified candidates with up-to-date knowledge and technical expertise only adds to the challenge. But fear not, at PeoplActive, we understand the critical importance of assembling a top-notch cybersecurity team. Our hand-picked professionals come with a proven track record in countering cyber risks and securing organizations’ most valuable digital assets.
With the right cybersecurity team in place, your organization can confidently navigate the complex digital landscape, protecting what matters most. Don’t compromise on security – connect with PeoplActive today and hire a cyber security expert from our 4000+ pre-vetted professionals to fortify your organization’s defense against cyber threats. Together, let’s build a fortified shield against the ever-evolving landscape of cyber risks, ensuring your business thrives safely in the digital world.
Kartik Donga
Founder & Strategic Defense Architect, PeoplActive
Kartik Donga
Founder & Strategic Defense Architect, PeoplActive














