How safe is your digital data? Digital transformation is significantly modifying each part of how the present organizations work and store business data. Businesses are whole-heartedly dependent on the data they retrieve from IoT devices and other sources. A single vulnerability is enough to sink the brand name and spoil the hard work of the whole workforce. When it comes to data security, you must have often come across two terms – Information security and cybersecurity. Do you think they are the same? No, they may share some similarities but can’t be put in the same shoes. In this blog, we would be discussing difference between cyber security and information security, where do they overlap, and where to Hire Cloud Cyber Security Expert and more on information security vs cyber security.
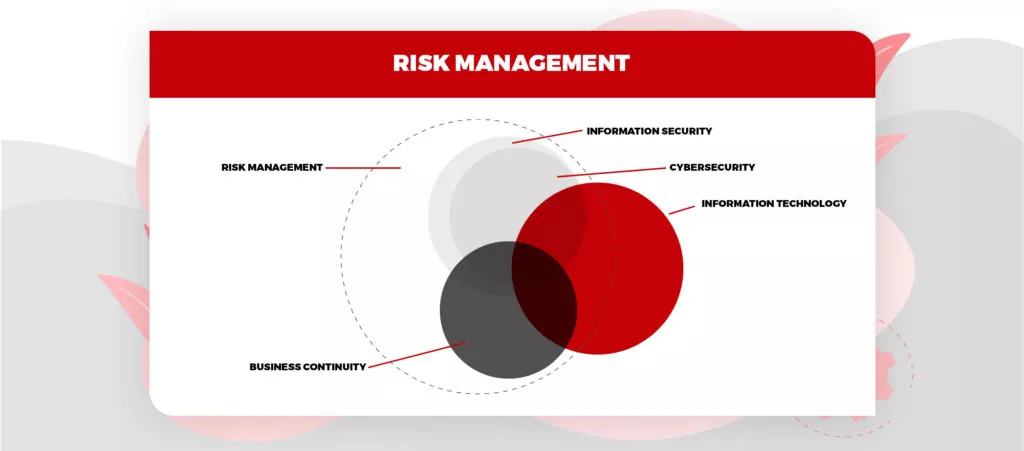
Image Source: Advisera
Cyber Security vs Information Security: Definition
What is Cyber Security?
Cyber Security is the ability to secure digital information stored in servers, PCs, cell phones, networks, and other electronic gadgets, from cyberattacks. Recognizing the sensitive data, its residing region, the risk it is exposed to, etc comes under the horizon of cybersecurity. It aims to secure and shield critical data from unauthorized attacks.
Image Source: IBM
Also Read – Cyberattacks Are Inevitable. Is Your Company’s Cloud Storage Secure?
What is Information Security?
Today, most of the data stored are in digital form, but it was not the same a decade ago. Those were the times when data was stored in rooms and file cabinets protected by locks. Information security covers a much broader field than cybersecurity, as it not just protects the digital data but ensures the overall confidentiality and integrity of important data.
Information security Vs Cyber Security: Types
Types of Cyber Security
There are different types of Cyber Security practices that experts incorporate on daily basis to secure data.
Cybersecurity can be categorized into five distinct types:
- Network security
- Application security
- Cloud security
- Critical infrastructure security
- Internet of Things (IoT) security
- Network Security: This sort of security practices deal with securing networks from any unauthorized access and service interruption.
- Cloud Security: Cloud Security is a mix of several procedures, technologies, and policies that are intended to cooperate to keep cloud-based data and infrastructure secure.
- Application Security: This process assists with recognizing, fixing, and upgrading application security, empowering organizations to prevent hackers from stealing code and data present in the applications.
- Critical Infrastructure: It includes a blend of tools offering security services such as virus scanners, anti-malware software, etc.
- Internet of Things (IoT) Security – Each IoT device is considered a potential entry point into your database and a threat to your supply chain.
An organization should develop a plan that incorporates these five kinds of cybersecurity, however, there are additionally the three parts that assume dynamic parts in a network safety act: People, processes, and technology.
People
Most of the people aren’t deliberately bypassing security protocol – they either aren’t trained to do as such, or they aren’t taught regarding the meaning of their activities.
The following are five different ways the human factor can increase your cybersecurity risk –
- Suspicious URLs and Emails: Urge your staff to focus on URLs, delete emails that don’t have content or seem as though they are coming from a spoofed address, and stress the significance of monitoring individual data.
- Password Idleness: We know that sticking to the same password for a very long time isn’t suggested. Instruct your employees regarding the significance of regularly changing passwords and utilizing solid blends.
- Personal Identifiable Information: Employees must understand the need to keep their personal browsing such as shopping and banking assignments, limited to their own gadgets. Underline the significance of watching out for what sites might prompt others. What’s more, that incorporates online media.
- Backups and Updates: It’s genuine for an unsavvy tech consumer to approach their every day business without backing up their information consistently and refreshing their system’s anti-virus.
- Physical Security for Devices: How many of your employees leave their work area for gatherings, social events and mid-day breaks. Are they locking up their systems properly. Urge workers to safeguard their gadgets with as much consideration as they safeguard their things.
Processes
When workers outside of the IT department are trained, IT masters can focus on the process. The process by which cybersecurity engineers approach safeguarding confidential data is multifaceted.
Putting processes not just guarantees every one of these buckets is being consistently monitored, however, if online protection assaults occur, referring to a well-documented process can save your organization.
Technology
When you have systems and processes set up, it’s an ideal opportunity to ponder the tools to start implementation with.
Technology has a double significance with regards to your toolbox:
- The technology you’ll use to forestall and battle network safety assaults, like malware protection, antivirus software, DNS filtering, firewalls, and email security solutions.
- The technology your data resides on that needs your security, similar to PCs, savvy gadgets, switches, network, and the cloud.
Types of Information Security
Below are the various types of InfoSecurity that help associations secure their data:
- Access Controls: These controls are used to give access to business data in order to ensure confidentiality. These controls restrict the physical access of the clients for virtual access and the organization’s framework.
- Compliance Controls: They manage Cloud Cyber Security norms and protection laws that minimize the security risks. They implement prerequisites for information security and require information security risk assessment.
- Procedural Controls: These controls identify and minimize security risks to all the physical resources of the organization, including computer systems, data centers, and so forth. They additionally include security awareness education, compliance training, incident response procedures, and security framework.
- Technical Controls: Under these controls, multifactor validation (MFA) during login, in antivirus software and firewalls, and so forth, to add an additional security layer.
Cyber Security vs Information Security: Where do information security and cybersecurity overlap?
Do you still think that infosecurity and cybersecurity are same? But they are not, however they do overlap. Let’s dig deeper to understand what are those points cause some justified confusion about these terms.
You must be agreeing that most of the data is stored digitally (computer, servers, network, cloud). No doubt, it helps in accelerating the business operation but it also invites vulnerabilities if proper security measures are not taken care of.
Data is the biggest concern for both types of security. In information security, the primary concern is ensuring the confidentiality, integrity, and accessibility of the information. In cybersecurity, the basic concern is securing data against unapproved electronic access. In both cases, it is analyzed which data is more vulnerable and how a security framework is established with valid controls to avoid unauthorized access. Is cybersecurity part of information security? Yes, cybersecurity is a subset of Infosecurity. Now, let us find out the difference between information security and cyber security.
Also Read – Is Your Cloud Bill Too High This Month? That’s Probably Your Fault
Is Cybersecurity a good career?
Cloud computing is a versatile field having an exponential scope of growth. As every business is moving towards digitization, more and more data is being stored in cyberspace. This may put data in a vulnerable state if the security measures are not followed properly. That is why there is a huge demand for trained & cloud cybersecurity experts in the market who could assist organizations in managing and securing cloud data. Here are some profiles which are in demand –
- Cloud Infrastructure Engineer
- Cloud Architect
- Cloud Software Engineer
- Cloud Security Manager
- Cloud Developer
- Cloud Computer Systems and Network Administrator
- Cloud Automation Engineer
How PeoplActive Can Help You Secure your Cloud Data?
Post covid, Cloud migration has seen its peak. This quick transition has driven the attention of cybercriminals who are exploiting weaknesses present in cloud-based data to deploy malware. PeoplActive is a platform where you can hire Cyber security engineer within 48 hours of sharing your requisition with us.
At PeoplActive, you will get:
- Access to the remote team of top-tier cybersecurity experts across the world.
- Choose only the professionals that meet your business needs best.
- 100% dedicated team working on your cybersecurity needs to get it done promptly.
- Flexible hiring model– permanent/contractual roles.
Dear readers, we hope that you found this Cybersecurity Vs Information security blog informative and useful. To stay updated with what’s happening in the cloud talent-hiring market, do follow us on our social media handles and keep visiting the website regularly.
Submit your requisition and hire cyber security engineer in 48 hours.