Compliance should be a continuous process and not a reactive response! With new industry principles and administrative prerequisites affecting all industries, cyber security compliance turns into the main thrust for business achievement.
As the number and seriousness of digital assaults evolve, industries and governments try to authorize cyber security by setting up more tough compliance prerequisites. However, compliance prerequisites frequently fall behind cyber security risks. In this manner, to plan for changing cyber compliance necessities, associations need to make a security-first way to deal with online protection so they can stay ahead of the advancing prerequisites. In this blog, we’ll find out why is cybersecurity compliance important for businesses, where to hire a cybersecurity consulting team, the role of cybersecurity in compliance, 7 Steps to Creating a Proficient Cybersecurity Program, and more.

Image Source: Educba
In general, compliance in network security is characterized as keeping guidelines and meeting prerequisites. In cybersecurity, compliance implies making a program that builds up risk-based controls to ensure the trustworthiness, confidentiality, and accessibility of data processed, stored, or transferred.
In any case, cyber security compliance isn’t based on an independent norm or guideline. Depending on the business, various guidelines might be covered, which can make disarray and abundance work for associations utilizing a checklist-based methodology.
For instance, the medical care industry needs to meet Health Insurance Portability and Accountability Act (HIPAA) compliance necessities, however, on the off chance that a supplier also accepts instalments through a Point-of-Service (POS) gadget, then, at that point, it additionally needs to meet Payment Card Industry Data Security Standard (PCI DSS) prerequisites. Organizations that serve clients or work with people in the European Union should follow the EU General Data Protection Regulation (GDPR), and organizations meeting specific measures that have clients in California should consent to the California Consumer Privacy Act (CCPA).
Also Read – Top Cybersecurity Compliance Regulations Every Company Should Know
What types of data are subject to cybersecurity compliance?
Cyber security and information security laws and guidelines center around the assurance of delicate information, such as protected health information (PHI), personally identifiable information (PII), and financial information. PII includes data that exceptionally distinguishes an individual, for example,
- First and last name
- Social security number
- Mother’s maiden name
- Date of birth
- Address
PHI includes data that exceptionally distinguishes an individual, for example,
- Medical history
- Prescription records
- Insurance records
- Records of admissions
- Information about medical appointments
Sensitive financial data includes:
- Social security numbers
- Credit card numbers
- Bank account numbers
- Debit card PINs
- Credit history and credit ratings
Other sensitive data that may be subject to state, regional, or industry regulations include:
- IP addresses
- Marital status
- Race
- Religion
- Email addresses, usernames, and passwords
- Authenticators, including biometrics such as fingerprints, voiceprints, and facial recognition data
How do Businesses Benefit from Cyber Security Compliance?
Despite the fact that staying aware of the most recent cybersecurity compliance standards and rules can be costly, organizations should recognize that compliance carries huge advantages to the business. Let’s check out one by one –
Avoid fines and penalties
Failing to comply with the most recent principles and guidelines can prove costly for the organizations that wind up out of compliance. Accordingly, companies should know about the most recent compliance trends and enactments to stay away from fines and punishments. The absolute most normal compliances and their separate infringement punishments include:
-
- Health Insurance Portability and Accountability Act (HIPAA) – USD 100 to USD 50,000 for every infringement, with the greatest punishment of USD 1.5 million yearly
- Payment Card Industry Data Security Standard (PCI-DSS) – Between USD 5,000 and USD 100,000 every month
- General Data Protection Act (GDPR) – 4% of an organization’s worldwide turnover or 20 million euros, whichever is higher
California Consumer Privacy Act (CCPA) – USD 2,500 to USD 7,500 for each infringement
Build Customer Trust and Brand Reputation
The genuine danger of a data breach is not confined to business interruption and monetary misfortune however stretches out to the enduring harm it can have on brand reputation and client trust. During the hour of vulnerability and disarray set off by an information break, a strong reaction is basic to ensure client loyalty and brand reputation.
As per a new report by Deloitte,
- 59% of clients express that a single data breach would contrarily affect their probability of preferring the organization
- 51% of clients would excuse the organization that had a single data breach provided the organization rapidly resolves the issue
Remaining consistent with the most recent guidelines helps you find, decipher, and get ready for data breaches that can affect your business and harm your brand reputation and client trust. Data security consistency assists you with trying not to put your brand’s name in danger by convincing you to advise clients about a break.
1. Upgraded Data Management
To keep up compliance with information security guidelines, the associations should monitor what clients’ delicate data they assemble, know how and where they store the information, and access, deal with, and change that data in a streamlined way.
These prerequisites urge associations to adjust and upgrade their information the executive’s abilities to such an extent that it upholds security as well as works on functional productivity.
2. Upgraded Security
The compliance guidelines expect organizations to set up a network safety program, embrace an association-level online cybersecurity policy, and assign a chief information security officer. This will help in mitigating dangers and addressing data breaches.
3. Better Access Controls and Accountability
Cybersecurity compliances expect organizations to build up senior-level responsibility for the strategic management of cyber risk. Additionally, associations need to execute compelling and appropriate risk management frameworks to screen and control admittance to the security systems and databases containing critical data.
Also Read – A Savvy Guide to Pick the Right Cybersecurity Consulting Partner for Your Business
7 Steps to Creating a Cyber Security Compliance Program
1. Make A Team
Regardless of business size, you should in any case consider building a compliance team that will evaluate and screen network safety. Organizations keep on moving their basic business tasks to the cloud, that network safety will not (and won’t ever) exist in a vacuum. Along these lines, you’ll need to make an interdepartmental work process, and spread the word about that work process across business and IT divisions.
Risk investigation will assist your business with being more cybersecurity-compliant. Here’s how it works –
- Find out all data resources, the frameworks, and the information that they access.
- Evaluate the risk level of every information type by figuring out where high-danger data is put away, communicated, and gathered.
- Examine risk by utilizing the accompanying equation: Risk = (Likelihood of Breach x Impact)/Cost
- Set the risk resilience by deciding if to transfer, deny, acknowledge, or mitigate the risk.
3. Pick A Framework
Picking a system comes from understanding your danger profile. In that capacity, think about the below-mentioned points:
- Scope of coverage
- Amount of details
- Industry-specific terminology
- Taxonomy (overall arrangement of requirements & formatting)
A framework serves as a benchmark; notwithstanding, whichever system you use relies upon the environment of your business, implying that you ought to choose what’s significant for your association, just as its security and compliance objectives.
4. Set Your Controls
As you set up risk analysis, you’ll need to set up the controls to keep up with it and guarantee that you comply with cybersecurity. Presently, in view of your risk tolerance, you should decide how to moderate or move hazards.
Your controls can include:
- Firewalls
- Insurance
- Encryption
- Password policies
- Employee training
- Vendor risk management program
5. Set Up Policies
At the point when you set up strategies, you’re guaranteeing that the arrangements that you execute will comply with cybersecurity. Your policies will report your compliance activities and controls, in this way serving as the establishment for any audits (internal or external) that are important.
At the point when you make an effective cyber risk evaluation plan, it permits your association’s compliance group to change specific arrangements and strategies or to think of completely new ones. That is something worth being thankful for, on the grounds that numerous administrative bodies need their compliance division to furnish them with subtleties concerning how the strategies and methods can function with their installed cybersecurity programs.
7. Screen And Respond Nonstop
Since digital dangers keep evolving, all compliance necessities should do likewise. Cybercriminals are continually searching for better approaches to stealing information by utilizing existing methodologies, as opposed to tracking down new weaknesses. To stay ahead of cybercriminal activities, it is important for every organization to do continuous monitoring which detects threats.
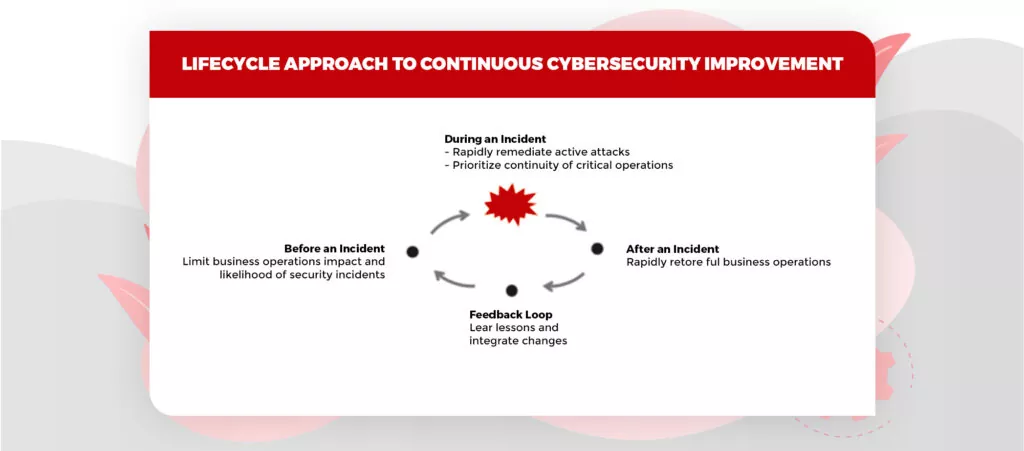
Image source: Microsoft
Where to hire a World-class Cybersecurity Team?
You must agree that a single cyberattack is enough to ruin the entire business. Then, why not be smart and work towards it? Every organization must understand the role of cyber security in compliance and maintain a cyber compliance team to look after the upcoming threats and protect business data from them.
Do you have a cyber security specialist team? If not, build one ASAP. You can hire a world-class cybersecurity professionals team – PeoplActive. Let us know your requisitions, we’ll get back to you soon.