Nowadays, a lot of sensitive and personal information is stored online and made accessible over networks. In order to secure their data and restrict access to only authorized individuals and entities, businesses must have strong network security. Only 14% of small businesses rate their ability to mitigate cyber risks, vulnerabilities, and attacks as highly effective.
The term “network security” describes the steps any business or organization takes to protect its computer network and data using both hardware and software systems. This seeks to protect the confidentiality and accessibility of the data and network. Every business or organization that manages a lot of data has a degree of solutions against various cyber threats.
Let’s take a look at why network security is so important for businesses in today’s digital age.
What is Network Security and Why is Network Security Necessary?
All the measures taken to safeguard a computer network’s integrity and the data on it are collectively referred to as network security. Network security is crucial because it protects sensitive data from online threats and ensures the network is usable and trustworthy. Multiple security measures are used in successful network security plans to shield users and companies from malware and online threats like distributed denial of service.

Also Read : Five Data Security Challenges and How to Address Them
Types of Network Security
To guarantee the security of networks and data, many elements in the field of network security work together. As a result, there exist various methods of network security:
- Virtual private networks (VPNs)
- Behavioral analytics
- Firewalls
- Intrusion prevention systems
- Wireless security
- Application security
- Access control
Virtual private networks (VPNs)
In most cases, a VPN encrypts the communication between an endpoint device and a network via the internet. Additionally, VPN enables experts to verify the connection between the network and the device. As a result, an online tunnel that is encrypted and secure is created.
Behavioral Analytics
Tools for behavioral analytics automatically identify actions that differ from the usual. As a result, your security team will be better able to spot possible trouble indicators of abnormal behavior and promptly eliminate risks.
Firewalls
A firewall is another common element of a network security model. They effectively serve as a gateway between a network and the internet. Data packets are compared against predetermined rules and policies by firewalls to filter incoming and, in some situations, outgoing traffic, preventing dangers from entering the network.
Intrusion prevention systems
IPS technology can identify or stop network security threats like brute force attacks, DoS attacks, and exploits of well-known vulnerabilities. A vulnerability is a flaw, such as one in a software system, and an exploit is an attack that takes use of that weakness to take over that system. These attacks can be swiftly stopped by employing an intrusion prevention system.
Wireless Security
In comparison to wireless networks, wired networks are less secure. You must have control over the computers and people who can access the network of your business. You should therefore have wireless security, especially because fraudsters are increasingly extorting people for their private information.
Application Security
Every piece of hardware and software used in your networking environment offers potential access points for hackers. Because of this, it’s critical to keep all programs updated and patched to stop cyber attackers from using security flaws to access sensitive data. Application security is the combination of hardware, software, and industry best practices you employ to keep an eye on problems and fill in security coverage gaps.
Access Control
This refers to restricting which users have access to the network or particularly sensitive areas of the network. You can limit network access to only authorized users and devices by using security policies, or you can allow guest users or non-compliant devices with restricted access.
Also Read: ZERO TRUST SECURITY: A New Perspective on Cybersecurity
Security approaches in network security
Level 1 – Minimal Protection
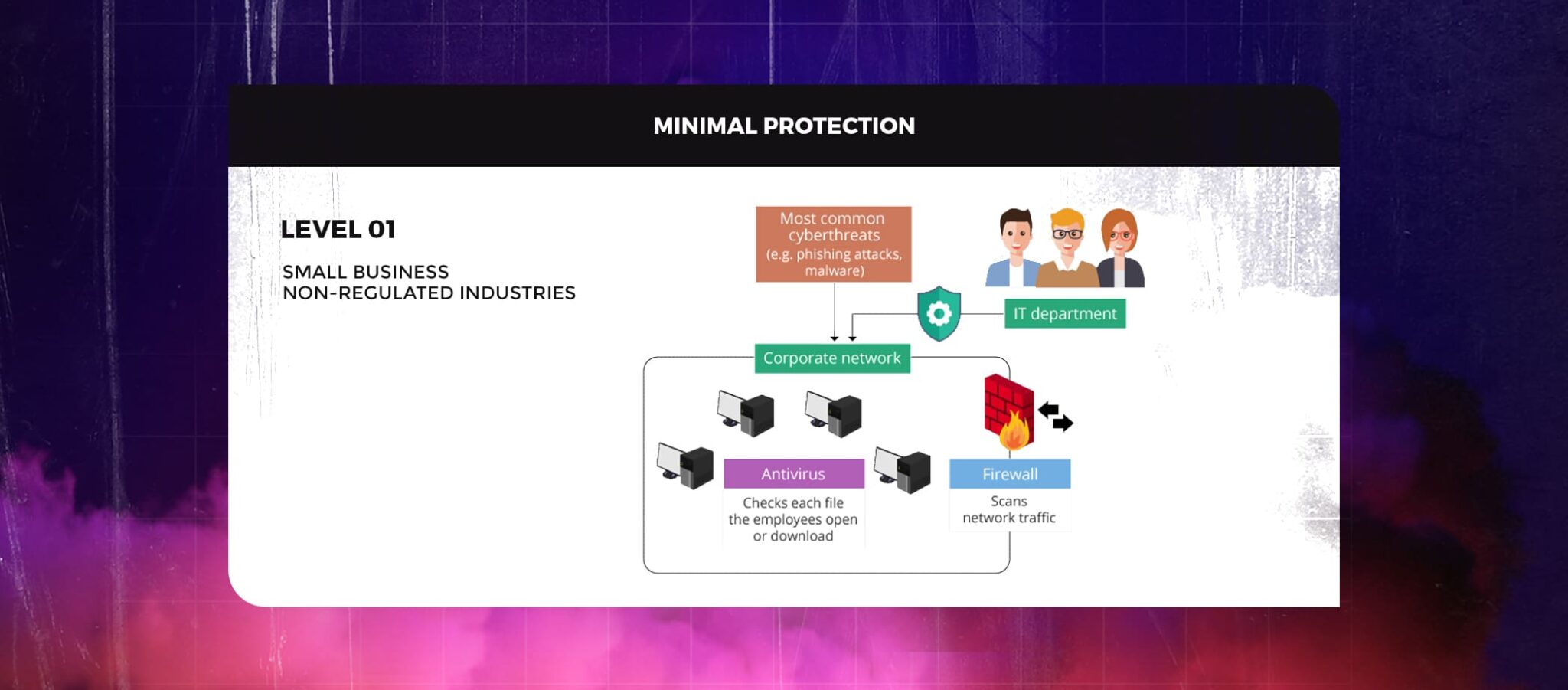
The main goal of Level 1 cybersecurity is to safeguard the corporate network from the most prevalent cyber threats, eg.., phishing attacks and malware.
Small enterprises that operate in unregulated industries with very constrained financial resources only receive minimal protection. Small, obscure businesses that don’t deal with data that hackers would find valuable (For instance, consumer personal information like passwords and credit card numbers) are unlikely to be the target of advanced cyberattacks like DDoS (Distributed Denial of Service) or spear phishing.
A properly configured firewall protection functioning in tandem with frequently updated antivirus software constitutes the bare minimum of cybersecurity measures required for implementation. Network traffic is scanned by firewalls to look for unusual packets or fragments of packets. By scanning each file that employees open or download from the internet or other sources, antivirus software ensures security from cyber threats including ransomware, worms, spyware, and other hazards.
No separate cybersecurity department needs to be set up to implement these security measures. The IT department of a corporation can be in charge of this as setting up firewall security, installing antivirus software, and regularly monitoring their performance do not require cybersecurity-related expertise. The yearly performance of these cybersecurity services won’t incur significant costs for a business with a tight budget. These actions can also assist system administrators in keeping track of emerging security flaws within the company’s network.
But a corporate network’s security should always be examined regularly. It is sufficient for a small business operating in an unregulated industry to perform vulnerability assessments and penetration tests once a year.
Level 2 – Advanced Protection
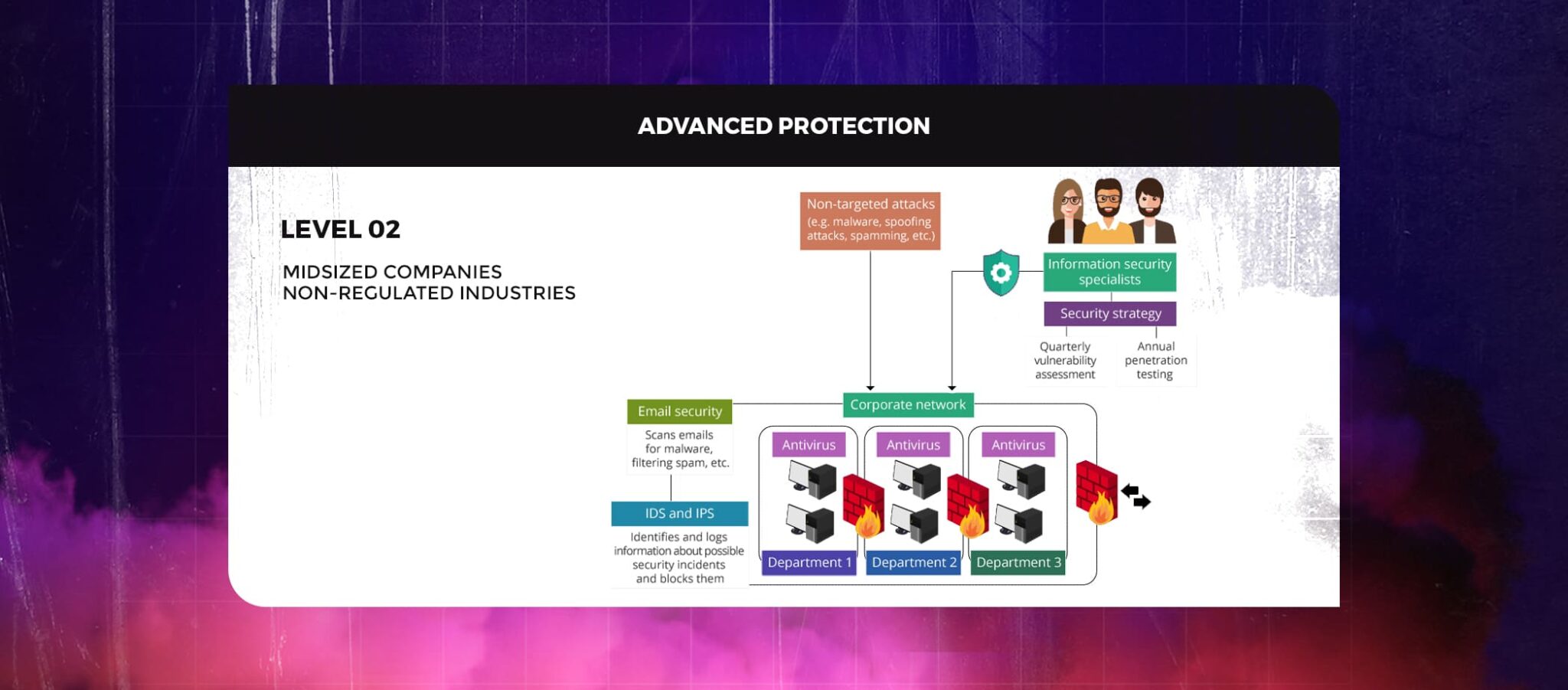
Level 2 cybersecurity guarantees the protection of the corporate network from untargeted attacks, such as viruses transmitted to a variety of email addresses, spoofing attacks, spamming, etc. In this instance, the attackers’ objective is to steal any important information from any IP address vulnerable to known security flaws that might be present in the corporate network.
Midsized businesses are very likely to become victims of untargeted attacks. Such firms may be inclined to overlook effective cybersecurity protections in their networks since they are not required to adhere to regulatory norms.
In addition to firewalls and antivirus software, the following items should be used to offer sophisticated network protection for the company:
Network segmentation, such as dividing the network into departments and connecting the segments with firewalls to prevent the movement of malicious code or other risks between the segments. Additionally, network segmentation entails dividing network assets that store a company’s data from portions that are external to the organization (web servers, proxy servers), lowering the risk of data loss.
Email security refers to a range of procedures (such as checking emails for viruses, blocking spam, etc.) used to protect business information from cyberattacks that use email as a point of entry (spyware, adware, etc.). The terms intrusion detection (IDS) and intrusion prevention system (IPS) refer to technologies that can detect potential security issues, record information about them, stop them before they propagate to other network settings, etc.
A business needs information security specialists to detect and manage cybersecurity risks, create security procedures and policies, and other tasks to maintain this level of network security. The business may set up its information security division for these goals or seek the help of a managed security service provider (MSSP).
Setting up a distinct information security department entails significant costs for both recruiting a skilled security team and purchasing the required hardware and software. Working with an MSSP is a more economical option that enables a corporation to keep its attention on its core operations. To manage the work with MSSP, the organization will still require an internal security officer.
A carefully planned security strategy should include quarterly vulnerability assessments and annual penetration tests to find, reduce, and manage cybersecurity risks to manage the effectiveness of cybersecurity protection. A company needs a cybersecurity strategy because it focuses on safeguarding the corporate network while taking into account employee BYOD (bring your device) usage, the widespread use of cloud computing, etc. It also gives clear instructions to staff members about appropriate behavior within the corporate network.
Level 3 – Maximal Protection
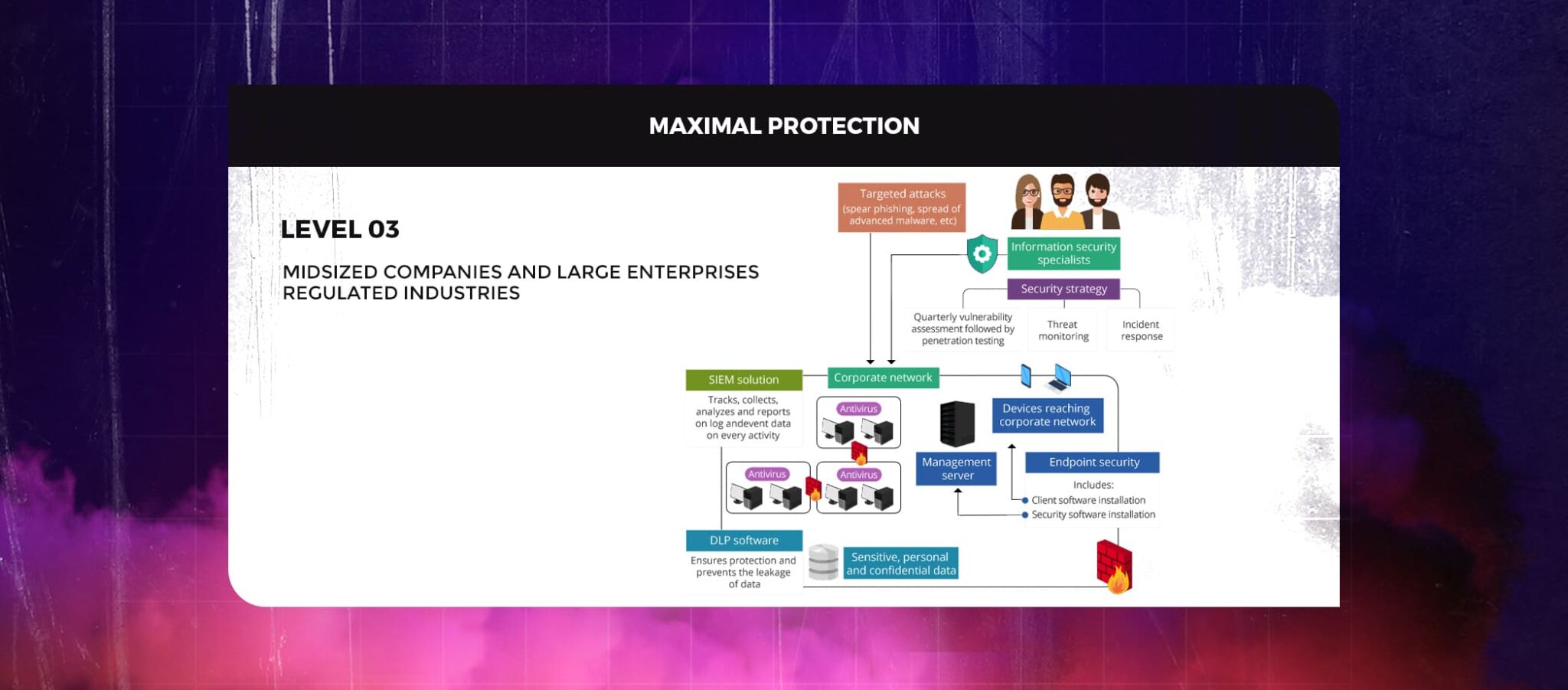
The main responsibility of Level 3 cybersecurity is to defend the corporate network from targeted attacks. This class of cyberattacks—spear phishing, the propagation of sophisticated malware, etc.—implies targeted efforts launched against a single company.
Targeted attacks typically affect large and midsized businesses, as well as government entities, that work in regulated fields like banking or healthcare. This occurs because the more data a business must safeguard (such as sensitive personal information, medical records for patients, information about financial accounts, etc.), the bigger and more tangible the effects of successful targeted attacks will be.
Companies working in regulated industries should give cyber threat protection their utmost attention to preserve compliance with laws and standards (HIPAA, PCI DSS, etc.).
The following cybersecurity elements could aid in preventing all potential attack vectors:
Security information and event management (SIEM). SIEM systems monitor, gather, examine, and report on log and event data on each activity taking place within the IT environment, preventing “I have no idea what happened” scenarios if the business’s network is hacked. Centralizing gathered log data, supporting compliance with PCI DSS, HIPAA, and other standards, and assuring real-time incident response are a few advantages of SIEM.
Endpoint security. This security strategy calls for securing every device—a laptop, a smartphone, etc.—that connects to the company network and could serve as a gateway for security threats. Endpoint security often involves installing specialized security software on a management server inside the corporate network in addition to client software on each device. By combining these measures, it is possible to keep an eye on what customers are doing when they connect remotely via their smartphones, tablets, and other devices to the company network. As a result, the business has superior real-time visibility into the full spectrum of security threats that it may need to handle.
Data loss prevention (DLP). Applying this strategy within a business operating in the financial or healthcare sectors is crucial. DLP software gives DLP administrators comprehensive control over the kinds of data that can be transported outside the business network, ensuring protection and preventing the leaking of sensitive, personal, and confidential data, such as customers’ credit card details, social security numbers, etc. DLP may reject efforts to upload company files to free cloud storage, forward any business email beyond the company domain, etc.
The combined efforts of a distinct information security department and assistance from an MSSP will be most helpful for correctly utilizing the security solutions listed above. Giving an MSSP complete access to, control over, and responsibility for sensitive data, customer personally identifiable information, etc., can be problematic for many businesses, especially in terms of security compliance. However, it makes sense to sign a comprehensive SLA with a provider of cybersecurity services and to assign some of the duties associated with cyber protection to an external MSSP. In addition to receiving security state monitoring and reporting around the clock, it also enables businesses to spend less money on cybersecurity protection.
Creating and maintaining a security strategy, carrying out vulnerability assessments followed by penetration tests every quarter (better done before each audit check to stay compliant with standards and regulations), making sure that constant threat monitoring is in place, and setting up a structured incident response are all necessary cybersecurity measures (IR).
To detect cybersecurity threats, such as infiltration attempts or data piracy efforts, threat monitoring requires continuously scanning the business network and endpoints (wireless devices, servers, mobile devices, etc.). With businesses increasingly hiring workers remotely and enforcing BYOD policies, the safety of sensitive data and corporate data is in danger on a larger scale nowadays, making threat monitoring even more crucial.
Security breaches that have already happened are dealt with by incident response (IR). To respond to cybersecurity threats with the least amount of damage and the shortest amount of recovery time, a firm needs a specialized in-house or outsourced team that is prepared for incidents, ready to identify actual occurrences, find the reasons, and respond to threats. IR initiatives stop minor problems from growing into more serious ones, like data leaks or system failures.
Summing it up
Corporate network security cannot be organized in a way that is universally applicable to all businesses. The selection of cybersecurity operations should be based on a company’s size, budget, and operating environment.
Applying firewall protection and antivirus software may be sufficient to safeguard the cybersecurity measures of a small corporate network if it is not necessary to secure the financial or personal information of their clients. The organization must be prepared to extend the cybersecurity measures and implement email security, network segmentation, endpoint security, etc. if it gains a major foothold in the industry they operate in and is at risk of becoming a target of cyberattacks. Installing DLP and SIEM systems can also become essential, especially for businesses operating in regulated sectors.
A business should regularly perform penetration testing and vulnerability assessments to maintain the desired cybersecurity protection levels.
A great strategy requires great execution also. Similarly to this, having a sound cybersecurity plan is insufficient; we also need a staff that can carry it out properly. Do you have a team like that? If not, PeoplActive can help you find the ideal cybersecurity engineer who possesses the precise qualifications you require. Send us your requests now, and we’ll help you find a cybersecurity expert tomorrow!





















