
In the digital era, security is a major problem that affects everyone. It should be your first concern to protect your company against malicious attempts and even rivals that try to make you feel inferior by pointing out security holes in your goods or services. There is a rising need for highly secure apps in the industry as a result of the rise in cyber threats. According to forecasts, the DevSecOps market would increase from its present value of USD 3.73 billion to USD 41.66 billion by 2030, with a CAGR of 30.76%. You can make sure that security is tested at every level of software development by using the DevSecOps pipeline, which enables you to spot problems as soon as they arise and fix them before they harm your reputation. The purpose of this blog is to discuss the key factors to take into account when setting up a DevSecOps pipeline in your company to enhance the software delivery process and raise the quality of the software provided to clients.
A successful DevSecOps implementation necessitates proper planning, a deliberate mix of cross-team collaboration, and a security-first mindset, and the end outcome is accelerated innovation.
Table of Contents
Toggle
Table of Contents
ToggleThe DevSecOps Pipeline: An Overview
The way businesses approach software development has completely changed because of DevSecOps. It is driven by the need to swiftly create new software that is resilient, agile, and devoid of vulnerabilities. A successful DevSecOps pipeline can assist businesses in incorporating security testing and feedback continually into the development process, which should lead to higher-quality code, fewer security incidents, and a faster time to market. An automated strategy called a DevSecOps pipeline helps businesses to create secure software during the development, testing, and deployment stages. A DevSecOps pipeline is put in place to make sure security flaws are found and corrected before the product is released.
Similar to the traditional SDLC process, which entails phases like planning, developing, building, testing, releasing, and deploying, a typical DevSecOps pipeline contains numerous stages. The DevSecOps approach has its own set of security checks.
- Plan: Create a test plan to specify the scenarios for where, how, and when testing will take place.
- Code: Add linters and Git controls to protect API keys and passwords.
- Build: Use Static Application Security Testing (SAST) tools to find bugs in code during the build process before moving on to the next step.
- Test: Use Dynamic Application Security Testing (DAST) technologies to check your app’s security while it’s running. The user authentication and authorization, SQL injection, and API-related components of these tools can all be used to detect issues.
- Release: Use security analysis tools to do rigorous penetration testing and vulnerability scanning before deploying the application.
- Deploy: Send a secure build to production after executing the above tests in production.
Also Read : It’s high time to take DevSecOps Seriously. And here’s why
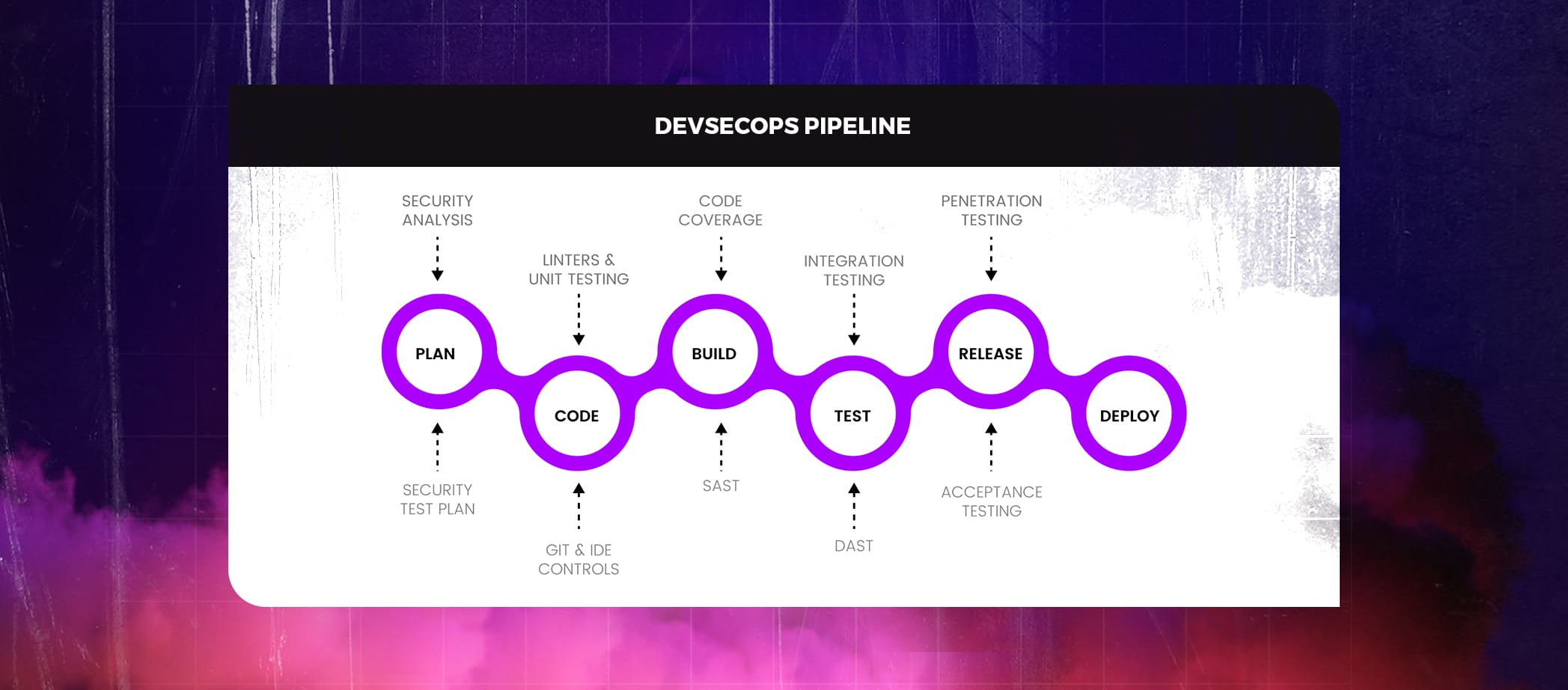
The most crucial factors to take into account while developing a DevSecOps pipeline
In Today’s fast-paced world, Organizations struggle to keep up with the demands of customers. Businesses are increasingly looking to DevSecOps as a crucial differentiator to stay competitive. But how can businesses make sure that their DevSecOps pipelines stages are effective? When developing your DevSecOps pipeline, keep these eight factors in mind.
Security scanners for containers
Applications are being deployed in containers, however, there are certain security risks. Scanning for vulnerabilities, malicious files, and compliance issues is essential as the number of container images grows. One of the biggest issues with container scanning is the detection of unknown vulnerabilities.
Pre-commit hooks and Security Plug-ins
Security measures could impede development, which is a serious concern for businesses and software engineers. Starting a DevSecOps pipeline with security checks causes a delay. The developer notices the potential vulnerability after submitting the code to the repository. IDE security plug-ins, pre-commit hooks, and other tools can speed up the process and deliver quick feedback. IDE security plug-ins locate security issues while the developer is working in their preferred IDE. If a developer’s code, a third-party library, or a package, contains a security vulnerability, plug-ins can notify them.
Automate CI security testing
To ensure the security of your CI/CD pipeline, use quality controls like automated unit integration and acceptance tests. The build process includes checking pre-built container images for known security issues.
Automate security tests in the acceptance test process
Automation is preferred when it comes to input validation features and checks for ensuring authorisation, authenticity, and identification. Functional security tests include establishing passwords and authenticating users, but non-functional security tests look for flaws in the program’s logic as well as the application’s and its infrastructure’s security.
Will DevSecOps replace DevOps in future?
Manage access controls for CI/CD
Access controls are employed in CI/CD pipelines to guarantee tool and resource security. This prevents any kind of incursion from affecting application development. A CI/CD pipeline should be secured by access keys, passwords, and other controls to ensure that only the team members who require it have access. By following these guidelines, it is possible to adhere to the notion of least privilege and reduce the possibility of an attacker acquiring access to a CI/CD system.
Static Application Security Testing (SAST)
Static Application Security Testing is a white box vulnerability screening tool that checks for vulnerabilities in an application’s source code, binary code or bytes of code. It aids in fixing underlying security issues by identifying the vulnerabilities’ root causes. SAST solutions scan without a running system and assess an application from the inside out. SAST lowers the chance of application security breaches by warning developers of potential flaws that might have been introduced into the code during development. It facilitates quicker vulnerability identification and collaborative auditing, allowing developers to learn about security while they are building. This enables developers to create more secure code, which in turn produces a more secure application. Users of SAST applications must comprehend that a single scan of the source code and subsequent bug fixes are insufficient to use SAST apps successfully. Delays and unsolvable problems will surely result from this strategy. The CI/CD workflow must incorporate SAST to prevent further delays.
Dependency management
External packages and libraries can speed up development by enabling developers to integrate functionality without having to create the entire code, but security considerations must be taken into account. Developer teams should be aware of the different parts that make up their applications and make sure that only secure, up-to-date downloads are made from reliable sources. It may be helpful to use programs like WhiteSource and OWASP Dependency-Check.
Ensure Pipeline Monitoring
Continuous monitoring of a DevSecOps pipeline security is necessary at the infrastructure, application, and network layers. This enables DevOps teams to continuously enhance their security decisions and stay ahead of the curve. Monitoring at all stages of your SDLC is made simpler by a wide variety of tools and technology. To keep track of networks, hardware, performance, and the status of running applications, procedures and tools have been put in place.
Also Read : CI/CD Pipeline – A Fuel to SDLC
End up creating your own DevSecOps pipeline for secure code delivery
Your business will need to get past certain major obstacles to properly utilize the DevSecOps pipeline. When you don’t know where to begin or what each stage entails, it is challenging to establish a pipeline from development to production with baked-in security.
For deploying DevSecOps, PeoplActive offers a whole solution. You can compete better in today’s fast-paced world by developing secure software rapidly and effectively. DevSecOps has the potential to revolutionize the commercial world. Although DevSecOps is certain to see some short-term failures, its long-term advantages are indisputable. If you need help in implementing a secure DevSecOps pipeline, connect with us here PeoplActive.
Get in touch
Hire DevOps & DevSecOps Developers


