
Will you sacrifice data security for the convenience of cloud computing? The Internet has started driving new technologies such as cloud computing that supports the virtualization of physical resources and accomplish multiple tasks simultaneously. Cloud users don’t need to buy underlying infrastructure and can go with the pay-as-you-use rule.
Cloud data is vulnerable to cyber threats and if cloud users don’t take proper security measures they can become a victim of cyber threats. Cloud data security can be ensured by secured data transfer, data integrity, and cloud data encryption. In this blog, we would be exploring varieties of cryptographic algorithms every organization must implement to ensure cloud security. So, let’s dig deeper and find why cryptography in cloud computing is worth a shot.
Table of Contents
Toggle
Table of Contents
ToggleWhat is Cloud Cryptography?
According to privacy experts, cryptography is the cornerstone of security. Cloud cryptography is the encryption of data stored in the cloud which adds a strong layer of protection and avoids a data breach. This practice safeguards data without delaying the data delivery. Cryptography expert Ralph Spencer Power said “Information in motion and information at rest can be better protected by cryptography. Virtual data needs to be stored cryptographically by maintaining the control of the cryptographic key.” Now, let us learn how to implement cryptography in the cloud and protect our cloud data.
There are two main types of Cloud Cryptography that organizations must incorporate in their Cybersecurity policies: data-in-transit and data-at-rest.
Data-in-transit refers to information that is divided into components that move between endpoints. It protects the information channels that a user encounters on the internet while they browse the page. This is accomplished by using SSL, a layer of encryption that surrounds an already secure channel. Hence, when data transfer between two endpoints of the website a user is accessing, the SSL encrypts both the user’s and the website’s data. In the case that one or more endpoints are hacked, Cybercriminals would only be able to access the encrypted data.
An organization’s storage of a sizable amount of corporate data on servers, disks, or the cloud is known as data-at-rest. Since protecting this type of data is crucial, all businesses should prioritize cloud encryption for at-rest data. It is feasible to authorize access to the encrypted material only through the decrypted credentials. If someone else tries to access this data, they will only see encryption metadata and not be able to access the plaintext.
Also, Read – Top 10 Cybersecurity Trends 2021
How to Implement Cryptography in Cloud Computing?
It’s not possible to control cloud data physically. Cloud encryption is a way of protecting data and communication with the help of codes. Cloud data encryption can guard sensitive data and verify asset transfer without delaying the information transmission. Several tech giants like Google and Amazon define cryptographic protocols for their cloud computing to balance efficiency and security.
There are different kinds of cryptographic keys used by companies for cloud security. Cloud data encryption depends on three algorithms:
- Symmetric-key
- Asymmetric key
- Hashing
Symmetric Algorithm
It utilizes one key for both encryption and information decoding. It doesn’t need a lot of computational power and works extremely high in encryption. Symmetrical algorithms consist of two-way keys to guarantee verification and approval. Except if the client has the key, the encoded information is put away in the Cloud, and can’t be decoded.
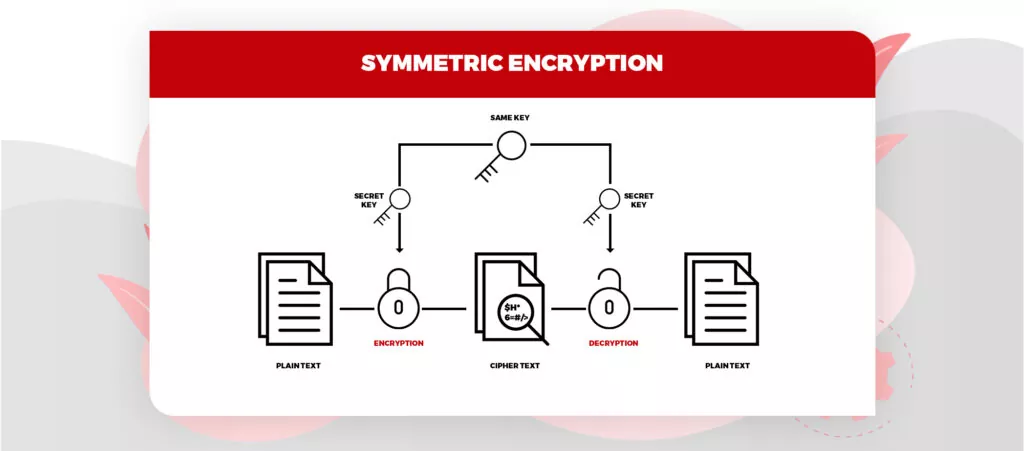
Image Source: SSL2buy
Some popular symmetric algorithms used in cloud computing algorithms are – Data encryption standard (DES), Blowfish, Advanced encryption standard, Triple DES, etc.
- Advanced Encryption Standard (AES) – It is used to encrypt digital data such as telecommunications, financial, and government. In AES, the same key is used for both encryption and decryption. It is a block of ciphertext that repeats itself after every defined step multiple times. It has a 128-bit block size, with key sizes of 128, 192, and 256 bits. It’s efficient in both software and hardware.
- Data Encryption Standard (DES) – It adopts a 64-bit secret key, out of which 56 bits are created randomly and the remaining 8 bits are used for error detection. DES is implemented in hardware and is basically used for single-user encryption, for eg – files stored on a hard disk in encrypted form.
Asymmetric Algorithm
It utilizes different keys for encryption and decoding. Here, every beneficiary requires a decoding key. This key is referred to as the recipient’s private key. Here, the encryption key belongs to a particular individual or entity. This sort of algorithm is considered the most secure as it requires both keys to get to a piece of explicit data.
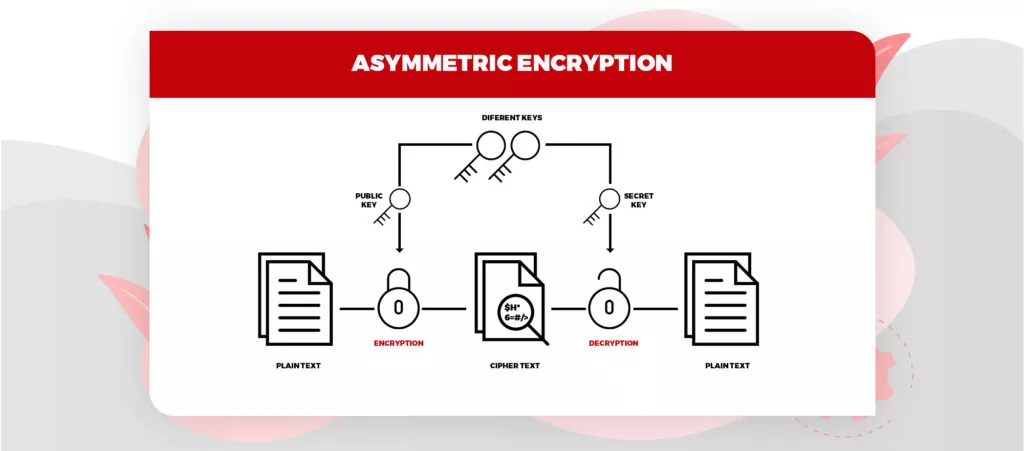
Image Source: SSL2buy
- Rivest Shamir Adleman Algorithm (RSA) – It is one of the de-facto encryption standards and is used for a variety of platforms. It used different keys for encryption and decryption. The public key is known to everyone and can be decrypted using the private key only by the authorized person.
- Elliptic Curve Cryptography (ECC) – ECC is modern public-key cryptography that depends on number theory and mathematical elliptic curves to generate a short key. ECC is preferred by security experts because of the small key size of the ECC.
Hashing
It is one of the major parts of blockchain security. In the blockchain, data is put away in blocks and interconnected with cryptographic standards like a string or chain. When an information block is added to the chain, a particular code or hash is assigned to the particular block. Hashing is basically utilized for ordering and recovering things in a data set. It likewise utilizes two distinctive keys for encrypting and decoding a message. It likewise gives quicker information retrieval.
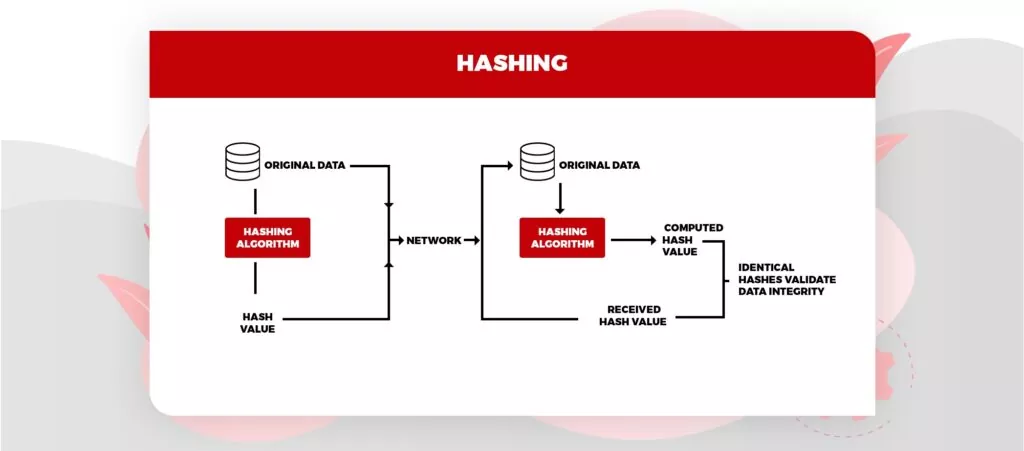
Image Source: Tutorialspoint
Advantages of cloud cryptography
- Cryptography in the cloud is probably the most secure strategy to store and move information as it complies with the limitations forced by associations like FIPS, FISMA, HIPAA, or PCI/DSS.
- The information stays private to the clients. Cryptography in the cloud lessens cybercrime cases.
- Companies get warnings promptly if an unauthorized individual attempts to access the data. The clients who have cryptographic keys are only allowed data admittance.
- The encryption keeps the information from being vulnerable when the information is being transferred from one PC then onto the next,
- Cloud encryption prepares organizations to stay proactive with all due respect against cyberattacks
- Receivers of the data can recognize if the information got is adulterated, allowing a prompt reaction and answer for the assault.
Also, Read – Hire the Top 5% Cyber Security Experts Your IT Team Needs
Disadvantages of cloud cryptography
- Cloud cryptography just grants restricted security to the information which is in transit.
- Cloud encryption needs exceptionally advanced systems to maintain encrypted information.
- The frameworks should be adequately versatile to update which adds to the involved costs.
Key Difference Between Symmetric and Asymmetric Encryption
| Size of cipher text | Smaller cipher text compares to the original plain text file. | Larger cipher text compares to the original plain text file. |
| Technique | old technique | Modern technique |
| Key Length | 128 or 256-bit key size | RSA 2048-bit or higher key size |
| Data Size | Used to transmit big data. | Used to transmit small data. |
| Algorithm | RC4, AES, DES, 3DES, and QUAD | RSA, Diffie-Hellman, ECC algorithms |
| No of Keys | Single | Two |
| Security | Less Secure | More Secure |
Using encryption and effective key management
In today’s technologically advanced climate, where every firm has sensitive data that any third party could misuse, IT teams most widely use Cloud encryption and raise widespread awareness of it. Users must utilize encryption as the default option for the data that is used more frequently. To provide this level of protection, Cloud service providers have encryption at rest on their desks and other critical media. Information and data are saved on disks in many regulated situations, and if they are not encrypted, they could be lost and result in significant financial and other repercussions.
Thus, it is crucial for organizations to carefully manage their keys. Key management is the most essential component of encrypting and safeguarding corporate data on the cloud. The majority of cloud service providers offer key vaults that can store sensitive data like API keys and other certificates to protect keys and maintain their administration.
How Can PeoplActive Address Your Cloud Data Security Challenges?
An organization can’t do without its employees. If you are operating a business on the cloud then you must have a team of cloud cybersecurity professionals who are well-versed with the latest techniques and tools to deal with unprecedented cyber threats. Well, PeoplActive can help you here. Being specialized in global cloud and cybersecurity staffing, we have a strong community of 4000+ cybersecurity and cloud experts all around the world looking for the next opportunity. If you want to beef up your team of cybersecurity professionals with experienced talents, PeoplActive can fetch you the best match within 48 hours. Do let us know your requisition today!
We hope you found the blog – ” Why Cryptography in Cloud Computing Is Worth A Shot?” useful and informative. To stay updated with the latest cloud news and amazing feeds on the cloud, keep visiting our website.


