
Application security was frequently neglected during the software development process. Testing typically wasn’t done until the very end. Unfortunately, when vulnerabilities were found at that point, engineers were forced to start over and rebuild a huge amount of code. This is changing as more businesses use the DevOps development technique to produce better software more quickly. The DevOps philosophy places a strong emphasis on addressing security at every level of the development lifecycle. Early and frequent software testing will help you find and fix bugs more quickly and cheaply.
Table of Contents
Toggle
Table of Contents
ToggleWhat is DevSecOps?
DevSecOps is the process of incorporating security into a pipeline for continuous integration, delivery, and deployment. By integrating DevOps values into software security, security verification becomes an active, integrated element of the development process. Similar to DevOps, DevSecOps is a technological and organizational paradigm that integrates automated IT technology with project management operations. DevSecOps processes incorporate active security audits and testing so that security is incorporated into the product rather than added after it has been created.
Teams should do the following to put DevSecOps into action:
- Incorporate security throughout the software development lifecycle to reduce vulnerabilities in software code.
- Assure that the entire DevOps team, including the development and operations teams, shares responsibility for adhering to security best practices.
- Automate security checks by incorporating security controls, tools, and procedures into the DevOps workflow at each level of software delivery.
Will DevSecOps replace DevOps in future?
How do you implement security in DevSecOps?
Every step of the standard DevOps pipeline, including plan, build, test, monitor, operate, deploy should be secured using DevSecOps roadmap. 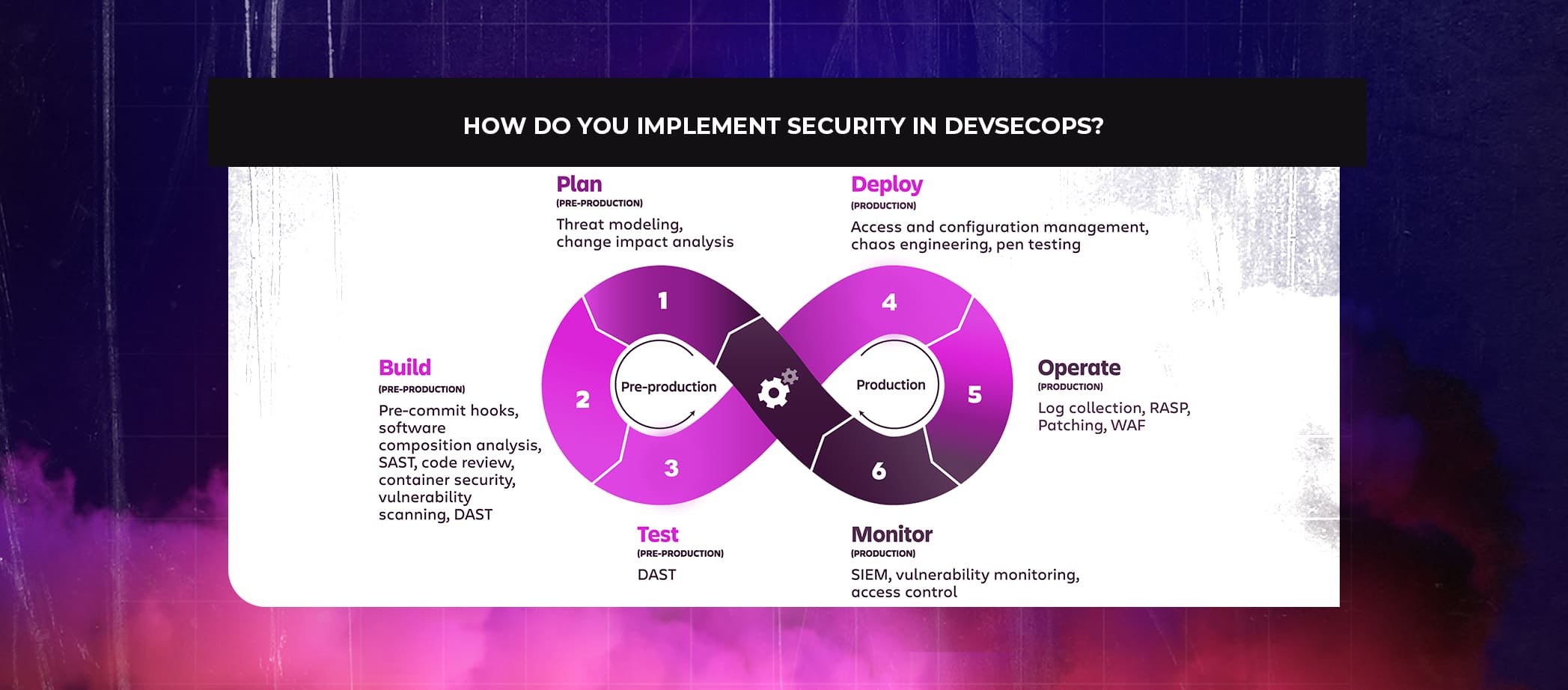
Plan
During the planning phase, key stakeholders discuss their vision for the project before developers start writing the code. Building a database of all security and compliance needs is one security strategy that makes sure they are taken care of throughout the development lifecycle. Automated threat modeling techniques are also used to spot potential flaws early in the development cycle and predict how an attacker might get into an application.
Build
Code is put through a set of automated tests once it has been written and committed to the source repository to find any bugs or potential integration problems. Static application security testing (SAST), which seeks to identify security holes in the source code, and software composition analysis (SCA), which provides visibility into open-source dependencies, are important security tests in this stage.
Test
Following approval, the code is released to a staging environment for additional out-of-band testing. The two important security checks during this stage are Dynamic Application Security Testing (DAST) and Interactive Application Security Testing (IAST).
Monitor
After apps are released and put to use, IT teams need to keep a security focus while continuously monitoring for problems and finding solutions. Solutions for information security continuous monitoring (ISCM) gather, match, and analyze security-related data from all areas of the application environment, such as servers and databases. This information is required to help with continuing risk management decisions.
Operate
The operations team now takes charge and puts a range of security policies in place to safeguard the application environment. A Runtime Application Self-Protection (RASP) tool is one of the most significant security solutions used here since it recognizes and prevents application assaults as they arise. Other significant security controls implemented during this stage include web application firewalls, endpoint detection and response tools, and app-based segmentation.
Deploy
The code is put to use in a real-world setting during this stage. This is the time when many businesses put into place a continuous integration and continuous delivery (CI/CD) pipeline that makes use of automation to swiftly update apps and bring new code into production. Additionally, information from a running system can be extracted using runtime verification techniques to find any security flaws.
In a Nutshell
To remain competitive, businesses must constantly develop their software, but security cannot be neglected. Delivering high-quality software with strong security is possible with a DevSecOps methodology.
PeopleActive provides a complete solution for deploying DevSecOps. We can assist customers in addressing their software needs with our DevSecOps methodology. Our methodology offers certain security tools and suggestions for each of the six phases of the DevOps development lifecycle. The commercial world might be completely transformed by DevSecOps. There will undoubtedly be some short-term setbacks for DevSecOps, but its long-term benefits are undeniable. Connect with us at PeopleActive if you require assistance in building secure applications using DevSecOps.
Get in touch
Hire DevOps & DevSecOps Developers




