‘If you fail to plan, you are planning to fail’. Without a proper cybersecurity program, you can’t guard your organization against data breaches, which makes it a powerful target for cybercriminals. Decision-makers can’t really exclusively depend on cybersecurity solutions like antivirus and firewalls as cybercriminals are getting smarter with their strategies each day.
Data theft is the fastest growing and the most expensive section of cybercrime. Cybercriminals are turning out to be more sophisticated, changing what they target and their strategies for attack for various security frameworks. Social engineering is the simplest type of digital assault with ransomware, phishing, and spyware being the easiest type of entry. Third-party vendors who process your information and don’t have strong cyber security measures are another normal assault vector.
If you’re not yet stressed over cybersecurity risks, you ought to be.
To help you understand the reasons of cyber security failures, we’ve compiled a blog explaining cyber security failures and how to avoid cybersecurity attacks. Also, how can you hire a cyber security specialist within 48 hours of submitting your requisition?
Table of Contents
Toggle
Table of Contents
ToggleSo, let’s begin…………..

Image source: Stealthlabs
Reasons for Cybersecurity Failures
There can be several loopholes that can make you fall into the cyberattack pit. Every organization has a different infrastructure and way of handling business data. Here, we will be listing out the possible reasons behind cybersecurity and information security failures.
1. You assume your business is too small to be on the attacker’s checklist
54% of private businesses assume they’re too small for a cyberattack, therefore, don’t have a proper setup for responding to digital attacks. This absence of—or even nonexistence of—network safety could be lethal for a business. Some of the private ventures don’t have a clue how to protect their assets from cyberattacks, and some don’t have strong IT security staff/workforce to deal with network safety measures and methods.
Also Read – Role Of Cyber Security In Compliance: A Comprehensive Guide 2022
2. You have an incomplete stock of resources and endpoints.
Many IT experts trust the utilization of bring-your-own-device (BYOD) during remote work has made them more vulnerable to cyber-attacks. More than 50% of remote workers use their personal devices to access the company’s network. Without a precise stock of resources, patches and updates go unmonitored, leading to an increase in vulnerabilities of such endpoints.
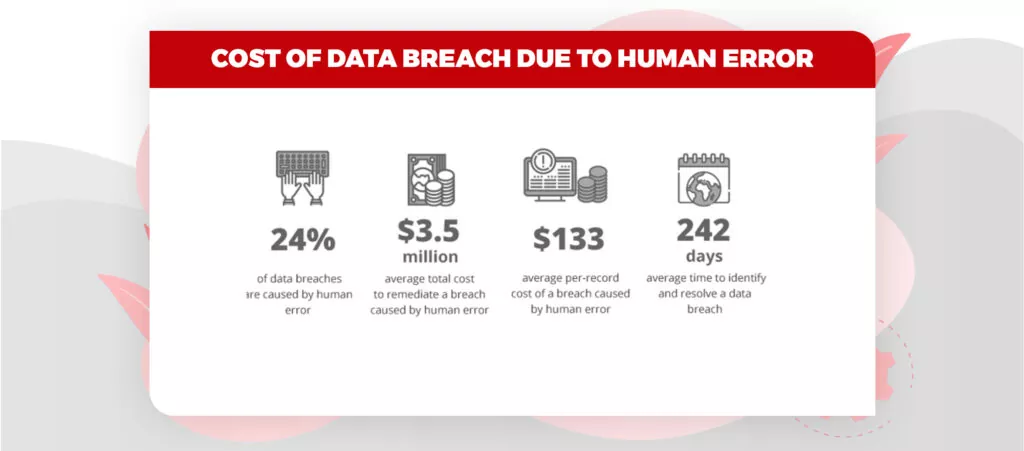
Image source: Ekransystem
3. You set it, and afterward, you fail to remember it.
Firewalls, antivirus, email security solutions are important, however, they’re not adequate. Organizations should fortify themselves by means of a multifaceted methodology. Rather than simply installing software, organizations should lead proactive safeguard measures, including regular vulnerability scans and infrastructure penetration tests
4. You disregard completing patches and upgrading on time.
When an organization finds a security imperfection, it develops a fix for it, which the end-user must install. In case the patch is not deployed, the chance of vulnerability increases. That is why it is important that organizations and end-users must install the update when it is delivered. 40% of organizations stand by to test and carry out patches to keep away from bugs.
5. You don’t understand your most prominent liability is your own employees.
Human beings are susceptible to social engineering assaults that maneuver individuals toward uncovering sensitive data. In 2020, phishing assaults increased by 11%.
6. You don’t have a reaction plan.
Having a proper incident reaction plan can set aside to $2 million on information breaks, as per IBM. But 39% of small and medium-sized organizations still don’t have an occurrence reaction plan. An occurrence reaction plan contains a methodology to isolate and eliminate the threat.
Hire On-Demand Remote Cyber Security Experts
What is the Impact of Cybercrime?
There are many factors that add to the cost of cybercrime. Every one of these elements can be ascribed to a helpless spotlight on best online protection rehearses. An absence of spotlight on cybersecurity can harm your business in many ways including:
- Economical – All sorts of misfortune results in loss to the economy of an organization. For eg – Theft of intellectual property and the cost of repairing damaged systems
- Reputational – When an organization faces a cyberattack, it loses the trust and confidence among its clients and people become hesitant to put further in the association.
- Loss of IP – Sometimes the Intellectual Property of an association like patent, copyright proprietary theft causes an enormous misfortune.
- Loss of sensitive business data – The information that has esteem in the worth of cash must be preserved however loss of such information can harm the association as it can be utilized by the competitors in the market.
- Trust Issues of Clients – Once an association faces a digital assault then clients do not have a good sense of reassurance with that association. It propels its clients to look for another vendor.
- Equipment Loss – Sometimes the malware destroys the entire system equipment so the association needs to spend a huge amount to reinstall them.
- Stock Prices – The attacker might decipher the stock costs of the organization to diminish the worth and picture of the specific organization by utilizing malware.
- Administrative Costs – GDPR and different data breach laws imply that your organization could experience the ill effects of administrative fines or authorization because of cybercrimes.
How to Minimize Cybersecurity Failure? Plan for it
The impact of a cyber attack can be lethal as it ruins the business’s reputation and brings in customer trust issues. Let us go through some of the major methods for how to prevent cybersecurity attacks.
Train Your Staff
Human error was found to be the reason for 90% of information breaks in 2019. If staff is trained how to distinguish and accurately react to cyber threats, most data breach incidents could be easily avoided. Such educational programs and training could likewise expand the worth of all network safety arrangement speculations since it would prevent staff from accidentally bypassing security controls that may facilitate cybercrime.
Ensure Your Sensitive Data
Invest in the latest tools and services that limit data misfortune, screen your third-party risks and consistently filter for data exposure and leaked credentials. Imagine what would happen if any data leak is left unattended? Surely, it could help cybercriminals break an organization’s sensitive assets. Therefore, it’s extremely important to implement a data leak discovery solution that observes loopholes all through the third-party networks.
60% of data breaches happen by means of compromised third-party suppliers, so by closing down vendor data breaches, organizations can prevent most of the data breach incidents.
Be proactive
Have an overall examination of your system and the sensitive data you hold. Ensure, as an association, you have a better understanding and visibility about the most critical data resources and guarantee they are properly secured. Make sure that patch and change management processes are in place. The biggest ransomware assault around the world to date (wanna cry) was pre-cautioned by Microsoft weeks before the assault – just those organizations who didn’t apply the patch were impacted.
These were some of the methods for how to prevent cyber security breaches. Implementing them can help you avoid scary cyber attacks.
Also Read – Is Your Company Following these Cyber Risk Mitigation Strategies
One of the biggest hurdles to secure infrastructure and business data from cyberattacks is the lack of a strong and experienced team of cyber security engineers. Businesses that are on the cloud need to have a cloud cyber security team that can offer bespoke solutions and think smarter than those of cyber attackers.
Are you looking for cloud cybersecurity experts? Leverage our pre-vetted talent pool of cyber security professionals and hire within 48 hours. Send us your requisition today, Hire tomorrow!


